In this write-up, we will explore how to effectively hunt for ransomware from a network perspective, focusing on identifying Indicators of Compromise (IoCs) related to LockBit ransomware. The scenario in module 4 begins when your Incident Manager informs you of a potential data exfiltration incident involving a compromised client device, prompting a deep investigation using network-related artifacts such as endpoint network logs and IDS packet captures.
Scenario: Network Compromise Detected
The target machine, CLIENT02, was compromised, and sensitive company data may have been exfiltrated. We are tasked with investigating network-related artifacts captured by IDS. As the Intrusion Detection System (IDS) logs full packet captures, we are confident that all attacker traffic has been recorded.
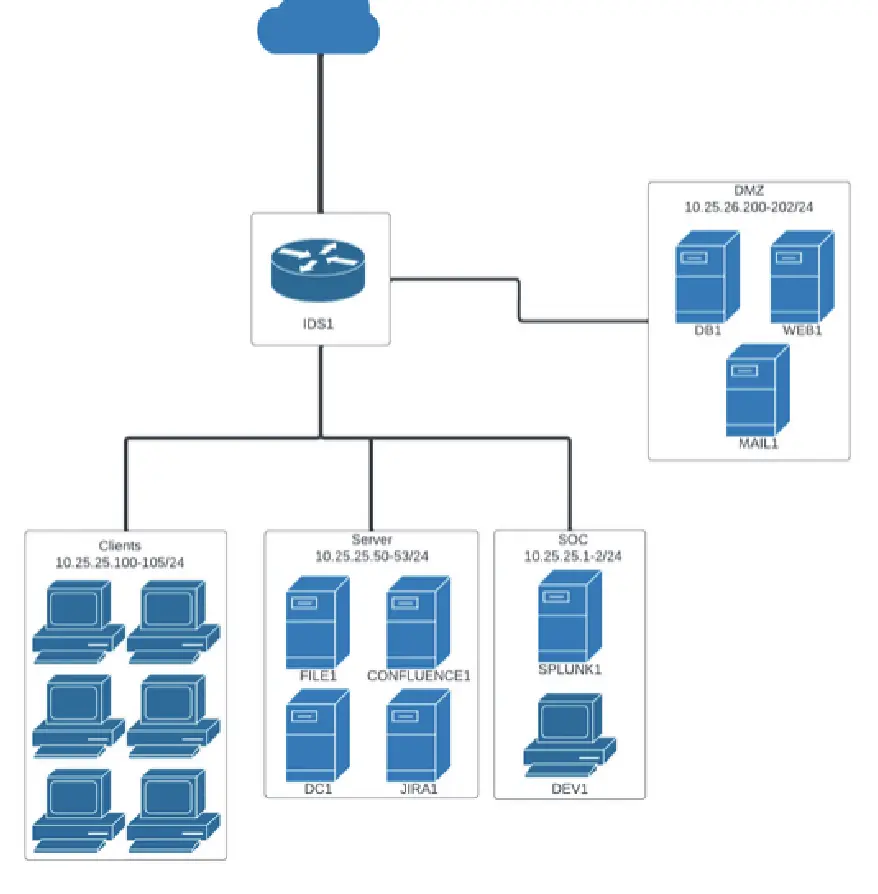
It has been established that the ransomware was executed on CLIENT02. Given that the IDS’s primary function is to store a full packet capture locally, we can be confident that the attacker’s traffic has already been recorded and requires analysis.
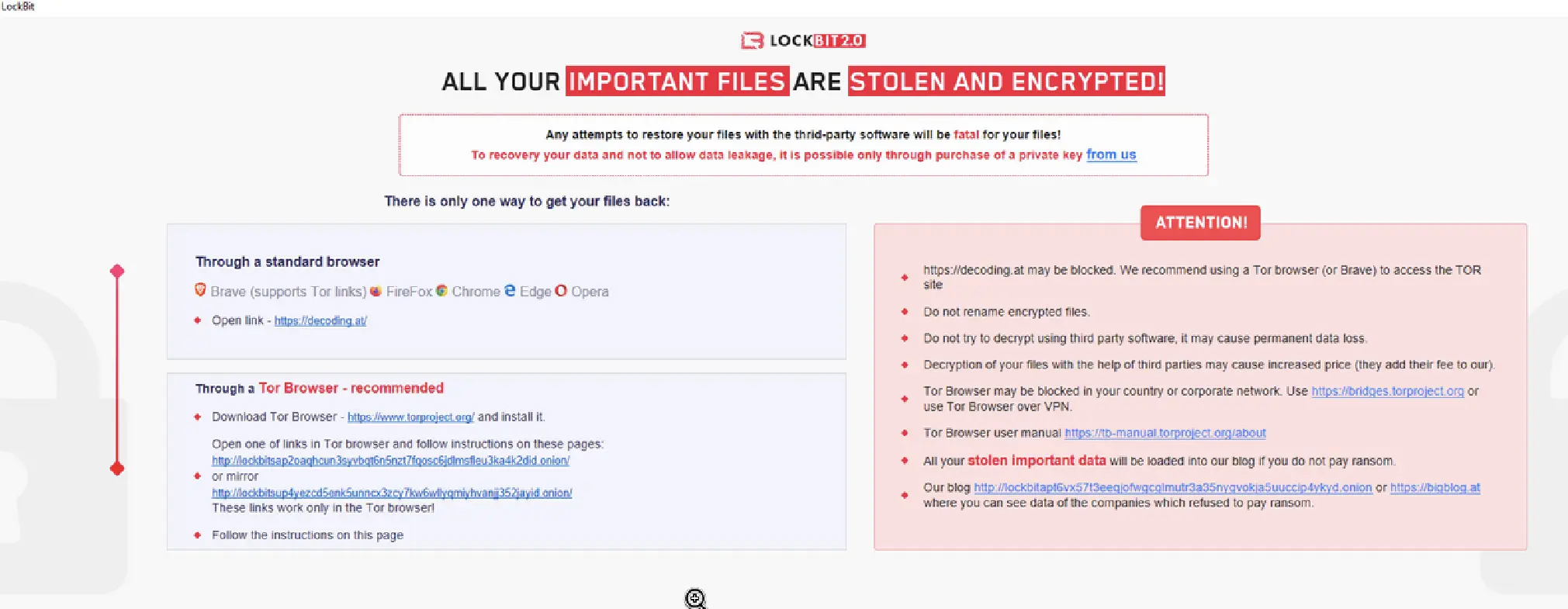
If a similar message appears on CLIENT02, we can infer that this is likely a LockBit attack. LockBit, a ransomware group that surfaced in 2019, is notorious for targeting enterprises and demanding hefty ransoms for decrypting files. LockBit 2.0, launched in mid-2021, includes enhanced features and capabilities.
Step 1: Initial Investigation Using Splunk
We begin by querying Splunk, connecting to it using a browser with valid credentials. The objective is to search for suspicious activity originating from CLIENT02.



