In this task, we will try to hack into a Linux system.
You can find the task here
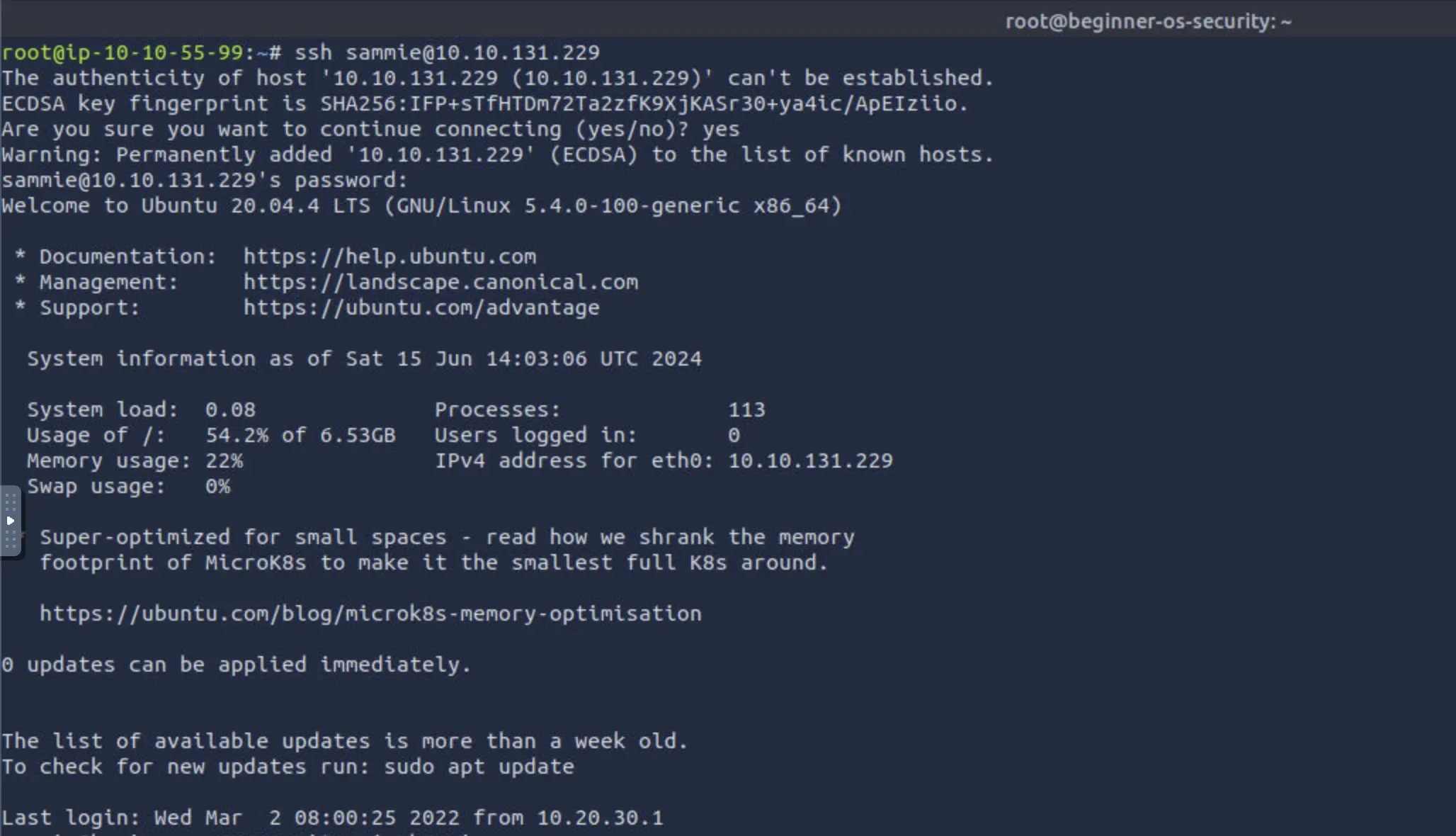
In this task on TryHackMe, the objective was to simulate a real-world scenario where we attempt to gain unauthorized access to a Linux system. We started by connecting to the target machine, identified by its IP address 10.10.131.229, using SSH. The login credentials were discovered from a sticky note found on a screen at the client's office—specifically, the username sammie and the password dragon.
The introduction to the room goes like this -
In one typical attack, the attacker seeks to gain access to a remote system. We can accomplish this attack by tricking the target into running a malicious file or by obtaining a username and a password. We will focus on the latter. After discovering a username, we will try to “guess” the password; furthermore, we will try to escalate our privileges to a system administrator. This account is called
rooton Android, Apple, and Linux systems. While, on MS Windows systems, this account is calledadministrator. The accountsrootandadministratorhave complete unrestricted access to a system.
Task descriptions include -
We were hired to check the security of a certain company. When we visited our client’s office, we noticed a sticky note with two words:
sammieanddragonon one of the screens. Let’s see ifdragonis Sammie’s password on the target machine10.10.131.229. From the AttackBox’s terminal, we will try to log in to Sammie’s account by executingssh [email protected]. The remote system will ask you to providesammie’s password,dragon.
We connected using the command ssh [email protected] and tried using dragon as the password. We confirmed we are logged in as Sammie using whoami command. After success login as sammie, we were instructed to explore further.

After confirming the connection, I looked for the questions that were asked in the exercise. First question was -
Based on the top 7 passwords, let’s try to find Johnny’s password. What is the password for the user johnny?
It was mentioned that two other user accounts, johnny and linda, might also have access to the system.
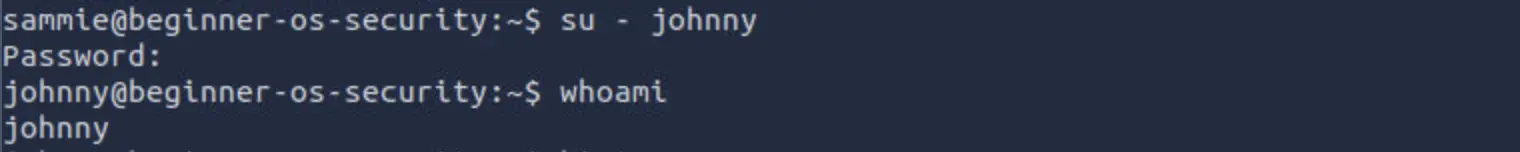
We tried with the command su - johnny to login as johnny and for the password we looked for a list of the 100,000 most common passwords that the National Cyber Security Centre (NCSC) has published.
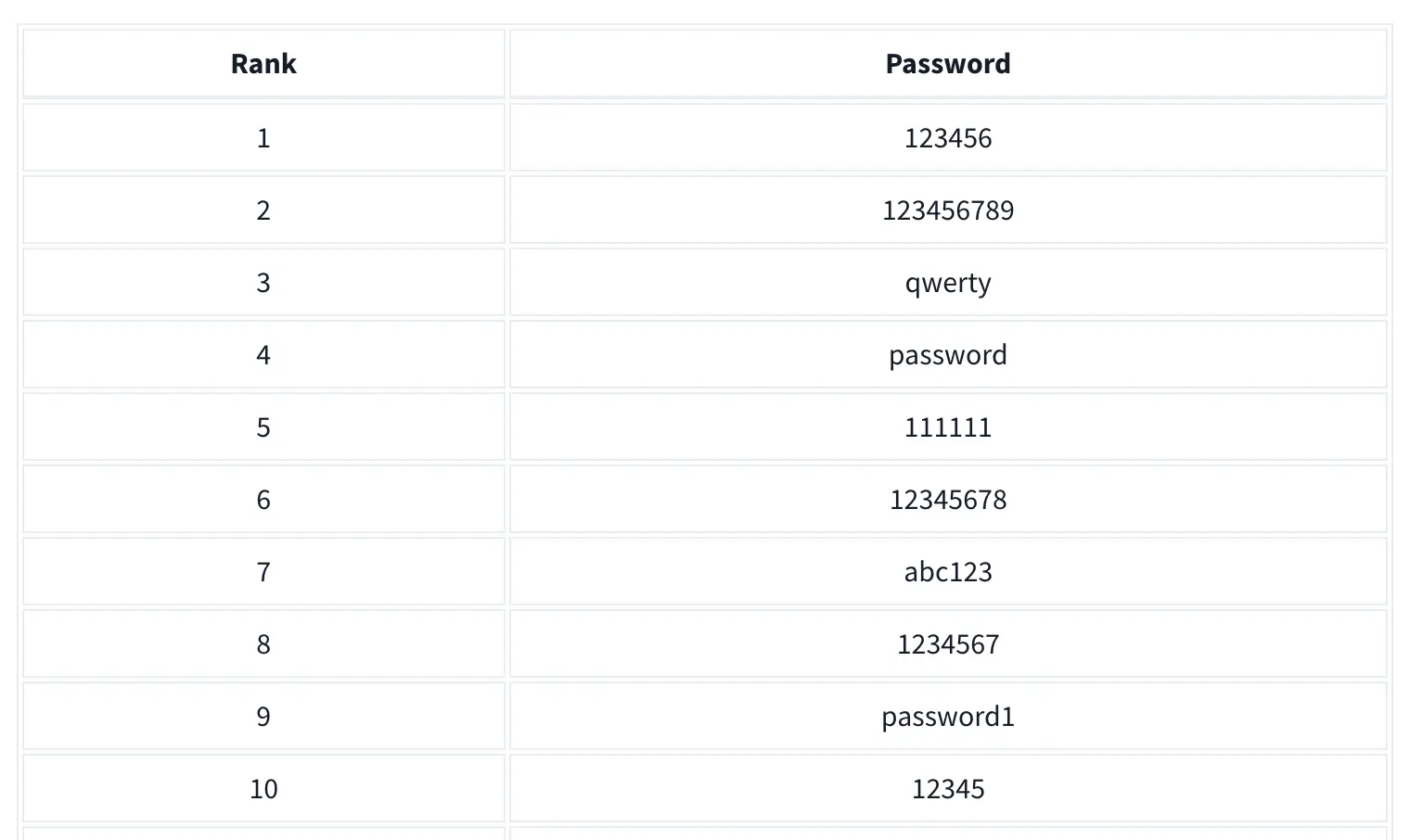
We wonder why the exercise asked to check for the top 7, and not top 10 or 5? Something fishy right? Following the hint provided in the task, we tried the seventh password from a well-known list, abc123, and gained access to johnny's account.
Now, moving on to the second question,
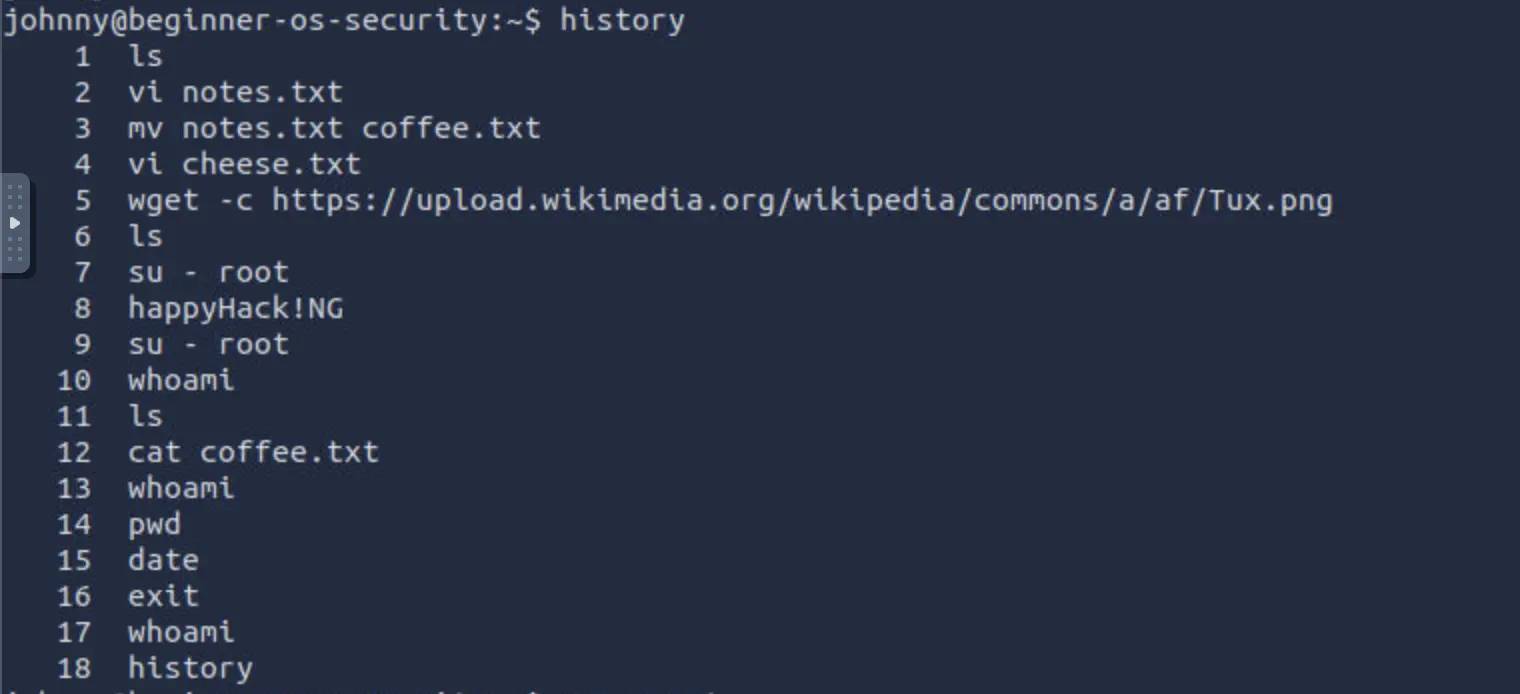
Once you are logged in as Johnny, use the command
historyto check the commands that Johnny has typed. We expect Johnny to have mistakenly typed therootpassword instead of a command. What is the root password?
Inside johnny's account, we checked the command history to find any clues left by the user. We discovered that johnny had mistakenly typed what seemed to be the root password, happyHack!NG, as a command. Armed with this critical information, we attempted to escalate privileges to the root account.
The final question was -
While logged in as Johnny, use the command
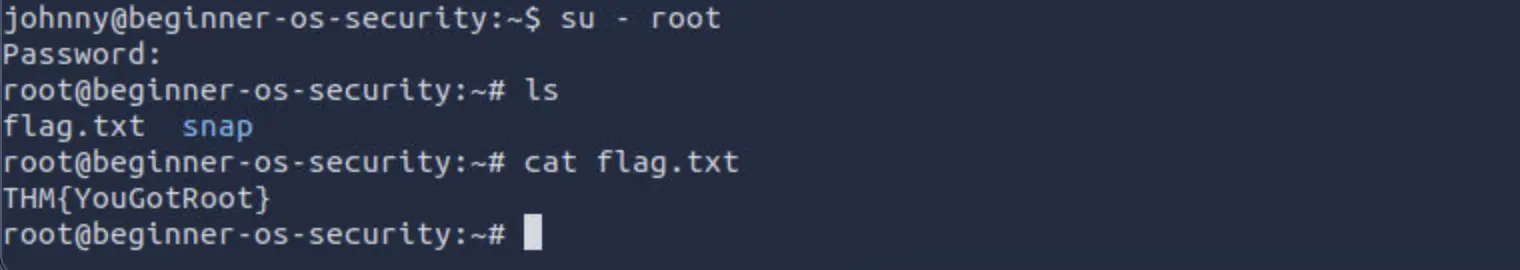
su - rootto switch to therootaccount. Display the contents of the fileflag.txtin therootdirectory. What is the content of the file?
Using the su - root command and entering the previously uncovered root password, we successfully elevated our privileges to root. From here, we navigated to the root directory and accessed the file flag.txt. Opening this file revealed the flag, which marked the successful completion of the task.
This exercise highlighted common vulnerabilities such as weak passwords and the importance of maintaining robust security practices. It also provided practical experience in basic penetration testing techniques, emphasizing the critical role of thorough reconnaissance and methodical exploitation in cybersecurity assessments.



