Continuing from my OffSec TH-200 journey…
In cybersecurity, ransomware remains one of the most dangerous threats facing organizations today. Ransomware attacks have evolved over the years, and attackers have become more strategic, organized, and persistent. In Module 2, Section 2 of the OffSec TH-200 course, I delve deeper into ransomware threat actors and their tactics, making it clear how these attacks are executed and why they’ve become so profitable for cybercriminals.
Let’s break it down, step by step.
Who Are Ransomware Threat Actors?
Ransomware actors are individuals or groups that use malicious software to block access to a computer system or data until a ransom is paid. Their primary motivation? Financial gain. These actors target everything from small businesses to large corporations, hospitals, and government institutions, demanding payouts that range from a few thousand dollars to millions.
But how do they manage to deploy ransomware into systems in the first place?
For ransomware to do its job, it first needs to be inside the target’s system. There are several ways this can happen:
Phishing attacks: The most common method. Attackers trick individuals into clicking on a malicious link or downloading an attachment that infects their device.
Exploiting vulnerabilities: Cybercriminals scan for unpatched systems or outdated software and use these weaknesses to inject ransomware.
Initial Access Brokers (IABs): Some threat actors don’t gain access themselves. Instead, they purchase access from Initial Access Brokers — specialized groups that sell pre-compromised access to systems. IABs play a crucial role in the underground economy by providing a shortcut for ransomware groups, allowing them to bypass the effort of breaking into systems themselves.
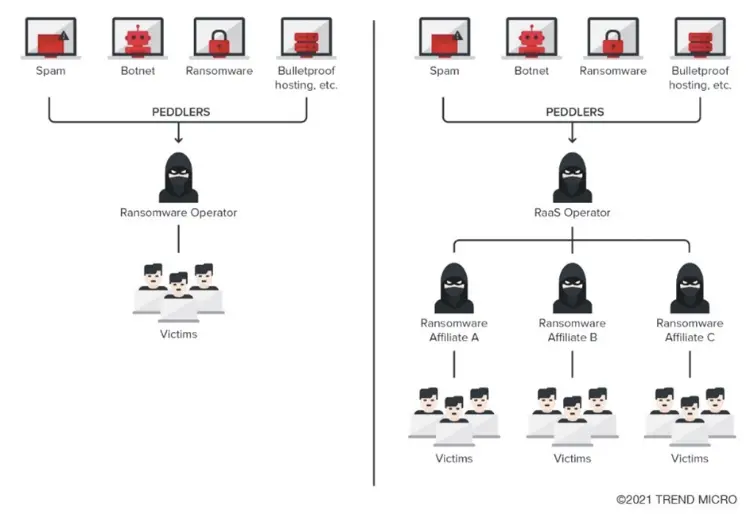
The rise of RaaS has significantly lowered the barrier to entry for cybercriminals. Much like Software-as-a-Service (SaaS), where companies offer software solutions on a subscription basis, RaaS is a business model where ransomware creators (called operators) sell or rent their ransomware to affiliates who then deploy it.
Operators often provide:
- Licensing models: Pay-per-use or subscription options.
- Profit-sharing: Affiliates pay operators a percentage of the ransom they collect.
- Support portals: Some operators offer technical support, tracking tools, and even customer service to help affiliates succeed in their attacks.
This system has created an ecosystem where even less tech-savvy criminals can profit from ransomware attacks without needing to write any code.
