Security Incident Summary
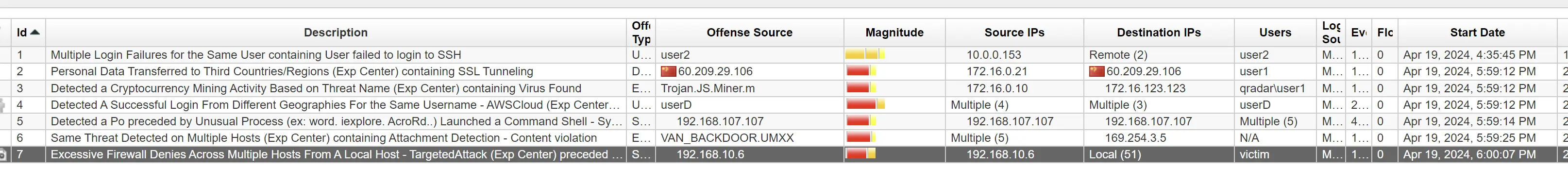
On April 19, 2024, between 4:35 PM and 6:00 PM, our network experienced a coordinated cyberattack involving multiple offenses. The incident began with over 109 million failed SSH login attempts targeting a Linux server. Following this, attackers managed to install a backdoor malware via phishing emails, which allowed them to gain persistence on multiple hosts. Subsequently, unauthorized AWS EC2 instances were created, and cryptocurrency mining malware was detected on the network. The attackers then conducted local scans, including database scans, and used FTP to download data from critical servers. Finally, data exfiltration to an IP address in China was identified, suggesting the culmination of their efforts to extract sensitive information. Despite the firewall blocking some traffic, it was unable to prevent all unauthorized downloads and data transfers.
Offense 1
Time of incident: Apr 19, 2024, 4:35:45 PM
Multiple Login Failures for the Same User
containing User failed to login to SSH
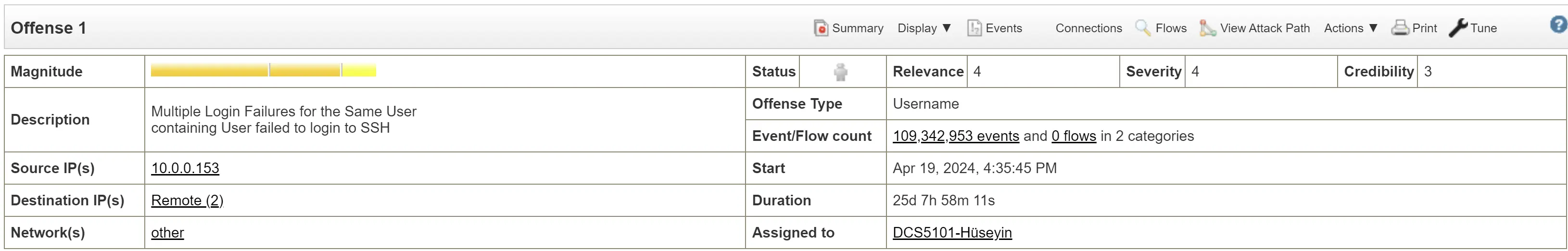
Targeted user: user2
Attempts First started on April 19th 2024 and have been going on until May 15th 2024
Over 109 million failed attempts for ssh (remote) and 6 failed user attempts.
Attempts to log into a linux server
[10] "Destination/Event Analysis". The number of events this source generated during this attack, was deemed worth a value of 10 on a scale of 0-10, with higher values indicating high volumes of events generated, and lower numbers indicating a smaller grade attack.
Of the 109,342,947 failed sign in attempts, the IP's that participated in the attack include but are not limited to:
- 10.0.0.153 (212,104 attempts for a single rule trigger)
Mitigation Strategy
Blacklist 10.0.0.153
Offense 2
Time of incident: Apr 19, 2024, 5:59:12 PM
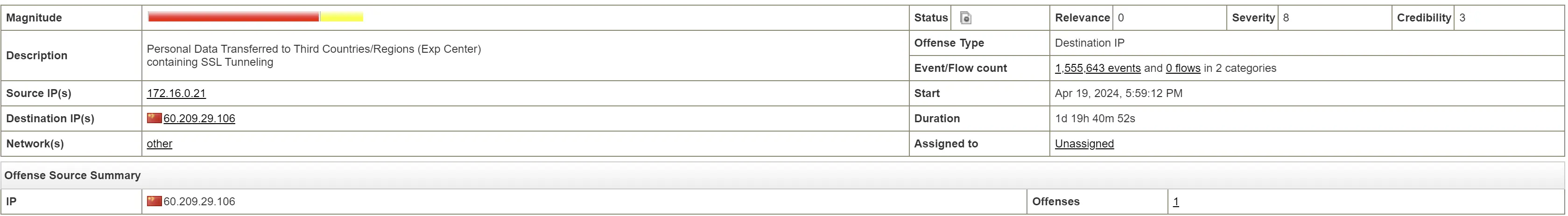
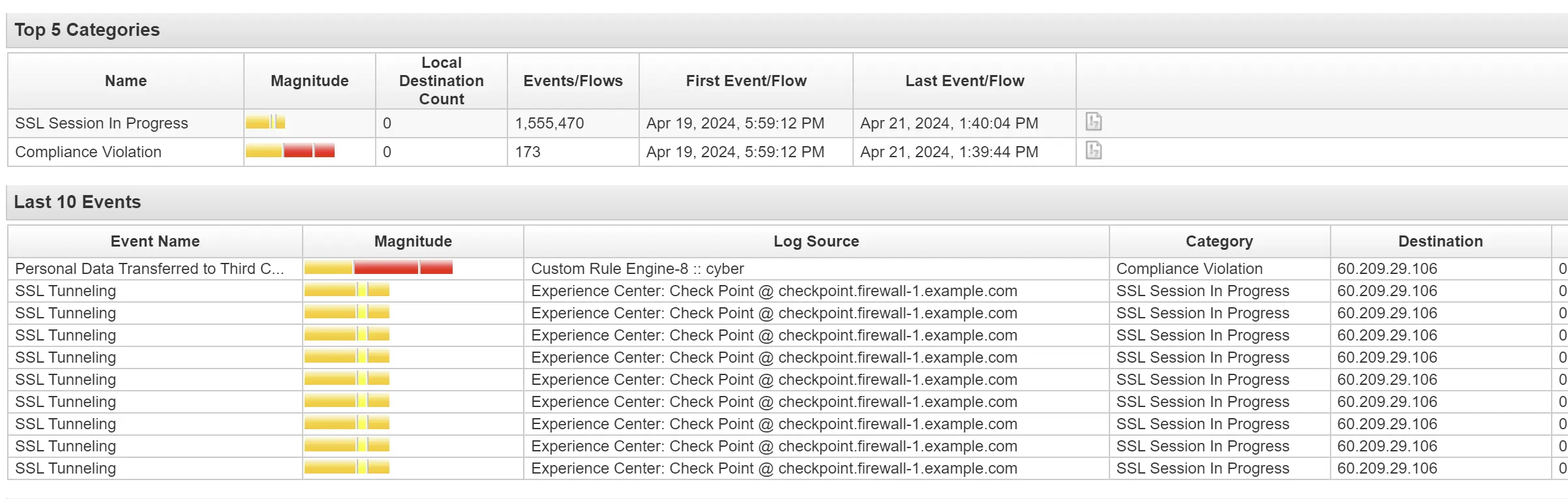
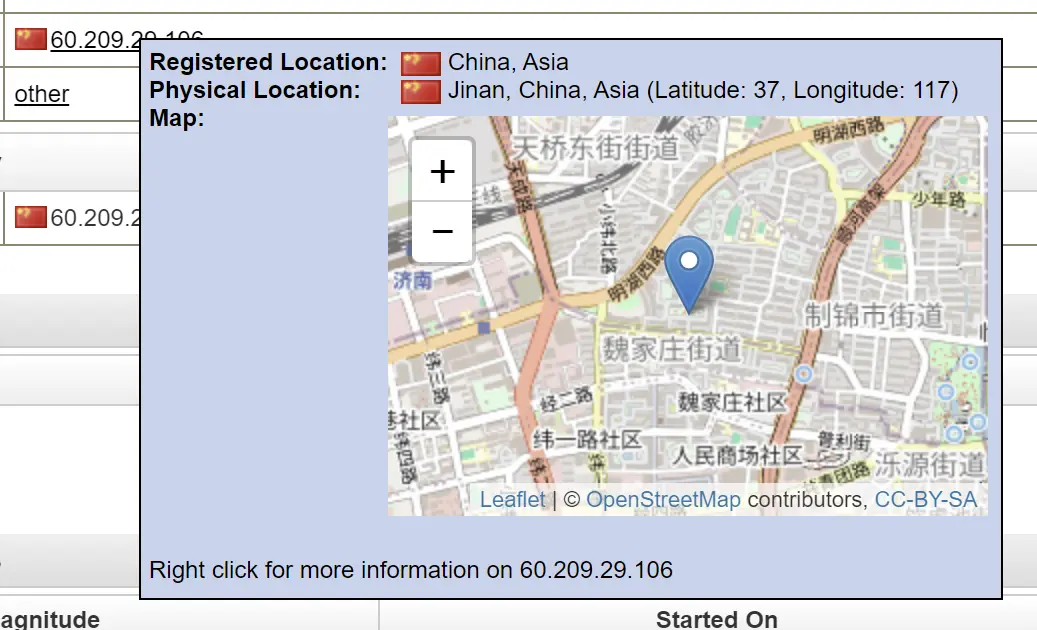
Attack IP: 60.209.29.106
Located in China
Rules
"CRE Event". CRE Rule description: [Personal Data Transferred to Third Countries/Regions (Exp Center)] Personal data are detected being transferred to Third Countries/Regions. Note that these countries/regions are defined in ECBB:CategoryDefinition: Destination IP is a Third Country/Region. Edit this Experience Center BB according to your business use case.
[10] "Destination/Event Analysis". The number of events this source generated during this attack, was deemed worth a value of 10 on a scale of 0-10, with higher values indicating high volumes of events generated, and lower numbers indicating a smaller grade attack.
[0] This source attempted to attack more hosts on the network than are known to exist. Approximately 0% of the destinations attacked, are thought to exist. The accuracy and scope of the attack is important to consider, as it may differentiate between a blind script-kiddie attack, and an accurate, intentional penetration attempt.
Not a intentional attack. Done via script
Offense 3
Time of incident: Apr 19, 2024, 5:59:12 PM
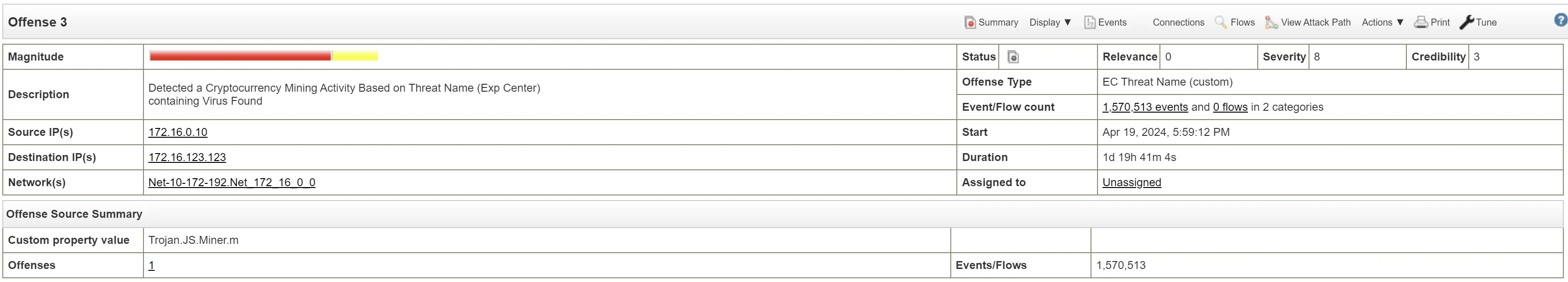
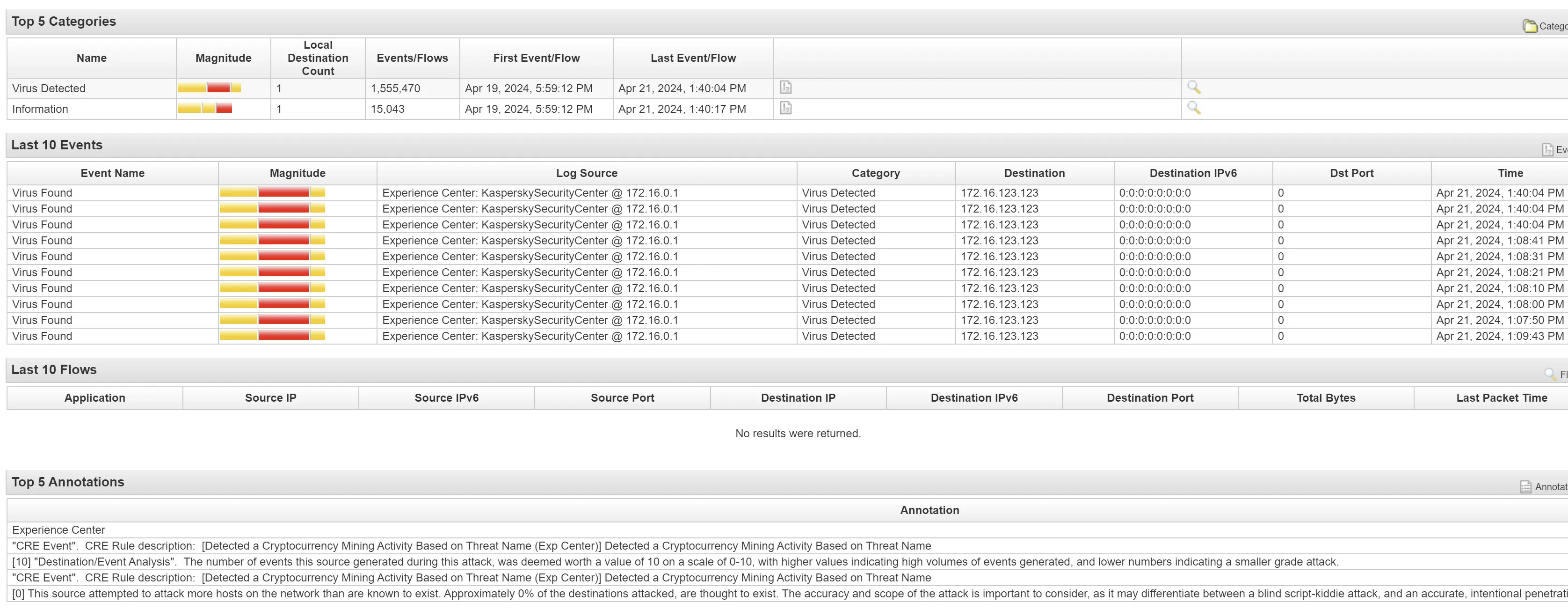
Malware name: Trojan.JS.Miner.m
Rules
"CRE Event". CRE Rule description: [Detected a Cryptocurrency Mining Activity Based on Threat Name (Exp Center)] Detected a Cryptocurrency Mining Activity Based on Threat Name
[0] This source attempted to attack more hosts on the network than are known to exist. Approximately 0% of the destinations attacked, are thought to exist. The accuracy and scope of the attack is important to consider, as it may differentiate between a blind script-kiddie attack, and an accurate, intentional penetration attempt.
Offense 4
Time of incident: Apr 19, 2024, 5:59:12 PM
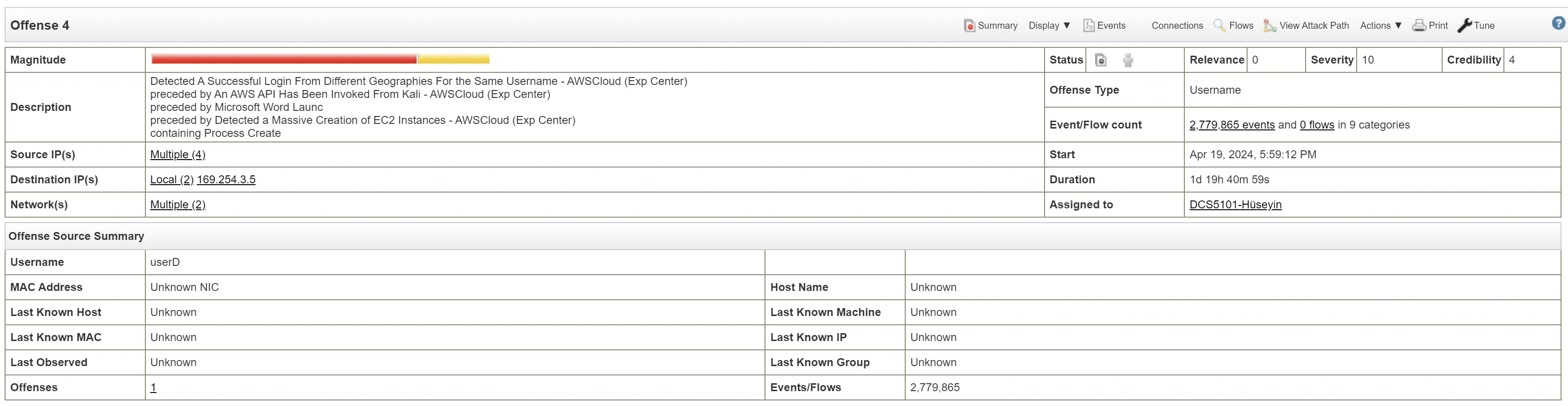
Login attempts came in from Russia, Finland, and 2 other IP addresses
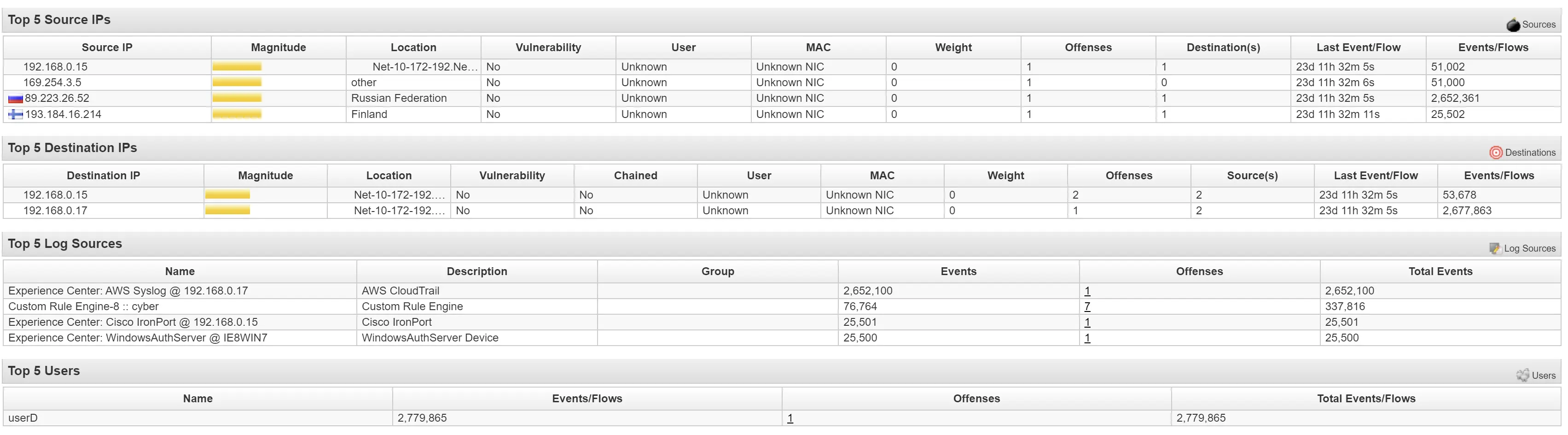
Logged in and created at least 7 AWS EC2 instances
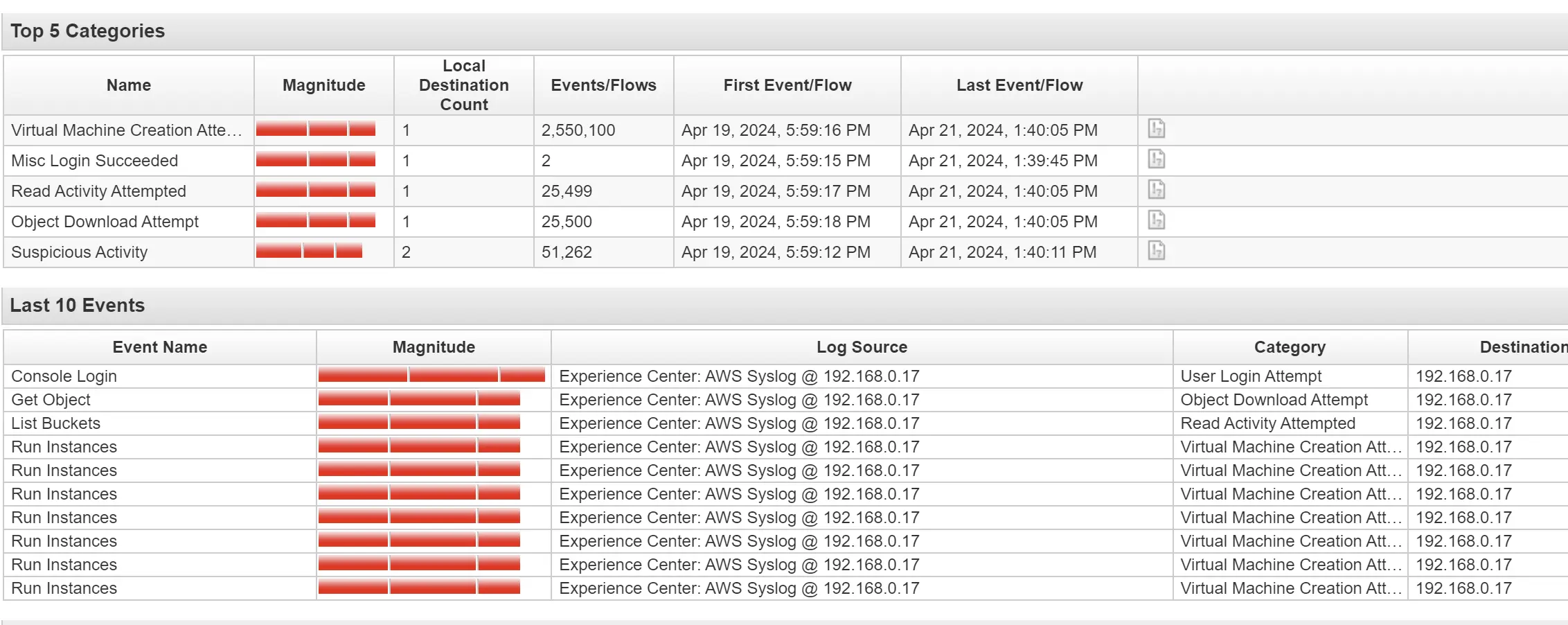
Offense 5
Time of incident: Apr 19, 2024, 5:59:14 PM
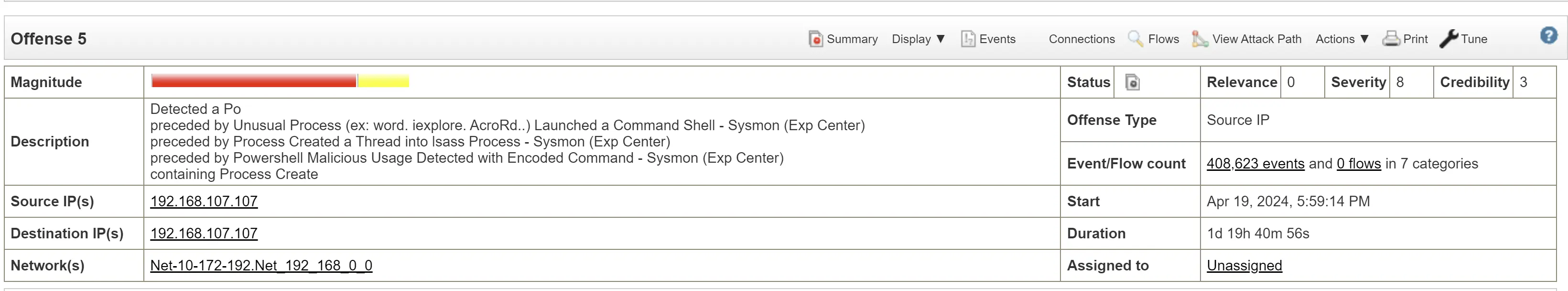
Target host: 192.168.107.107
Infected User: tiger
Possible escalation to system user
Detected a PowerShell activity:
-
Unusual Process Launch: Anomalous applications such as Word, Internet Explorer, or Acrobat Reader initiated a command shell. Refer to Sysmon for more details (Exp Center).
-
Process Injection: A process created a thread in the lsass process, which manages the OS security policy. Details can be found in Sysmon (Exp Center).
-
Malicious PowerShell Usage: Detection of PowerShell executing encoded (obfuscated) commands, potentially indicating a reverse shell or data dump. This includes the creation of background processes for malicious purposes. Refer to Sysmon (Exp Center) for more information.
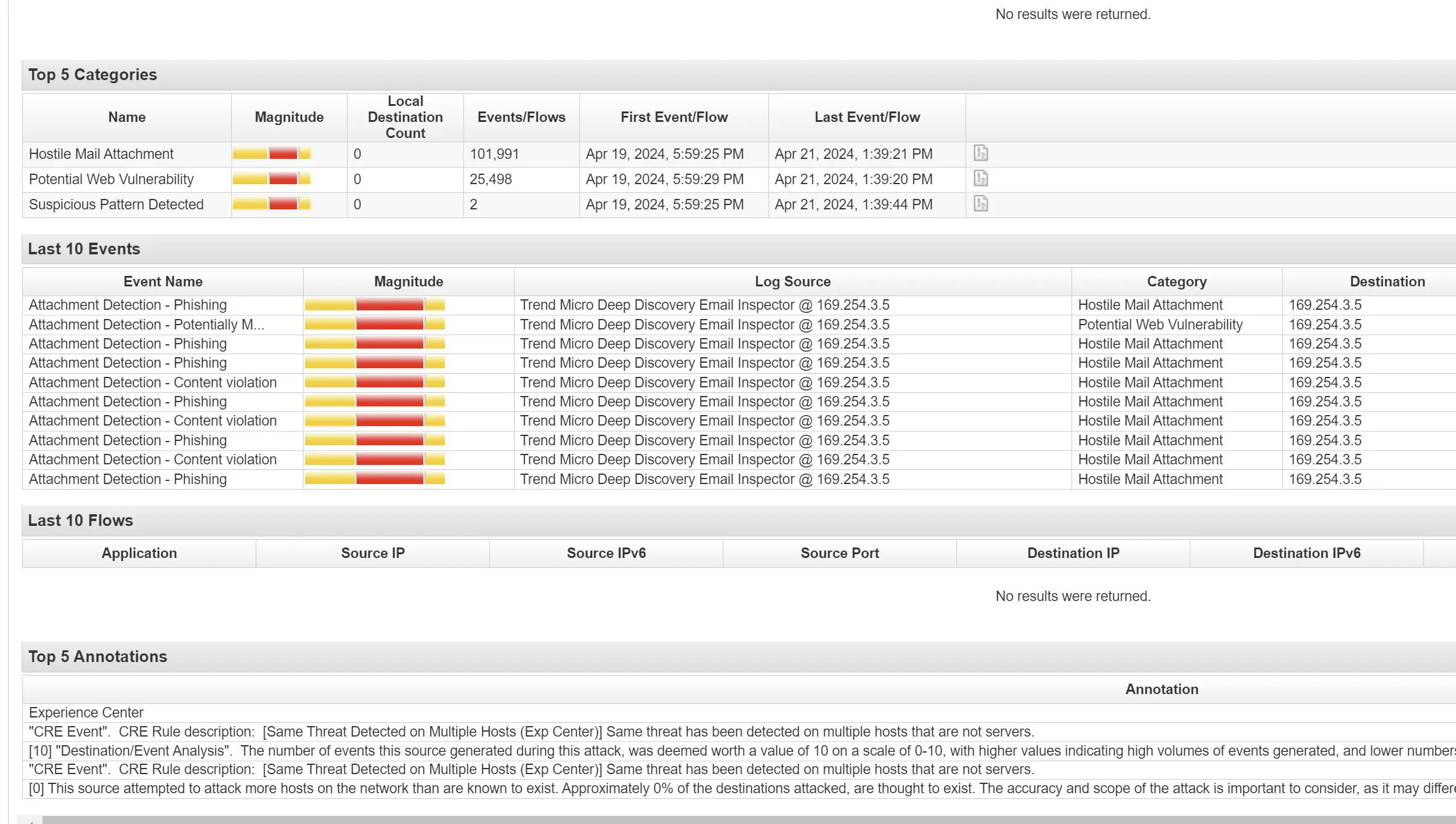
Categories of Security Events
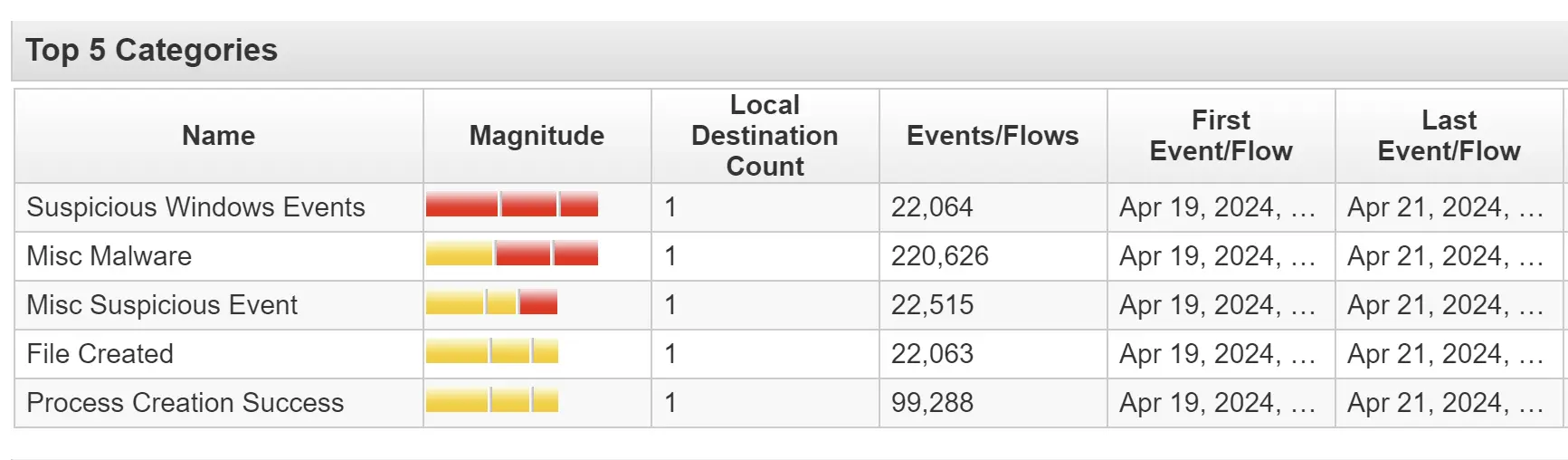
Detail of the rules that were triggered
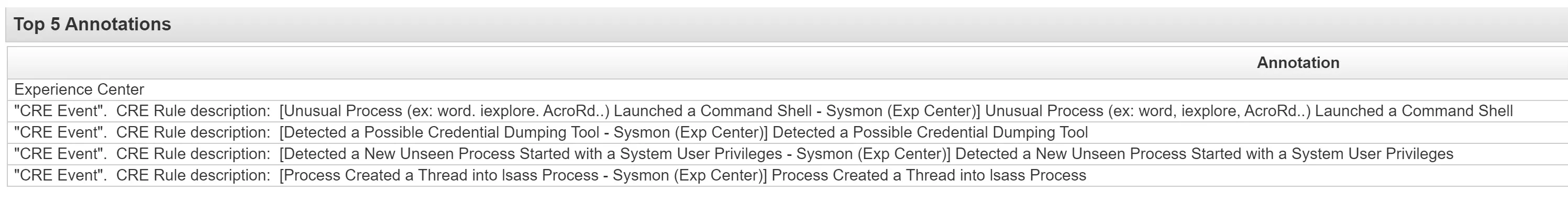
The following events all took place at the time of Apr 19, 2024, 5:59:46 PM
CRE Event". CRE Rule description: [Unusual Process (ex: word. iexplore. AcroRd..) Launched a Command Shell - Sysmon (Exp Center)] Unusual Process (ex: word, iexplore, AcroRd..) Launched a Command Shell
"CRE Event". CRE Rule description: [Detected a Possible Credential Dumping Tool - Sysmon (Exp Center)] Detected a Possible Credential Dumping Tool
"CRE Event". CRE Rule description: [Detected a New Unseen Process Started with a System User Privileges - Sysmon (Exp Center)] Detected a New Unseen Process Started with a System User Privileges
"CRE Event". CRE Rule description: [Process Created a Thread into lsass Process - Sysmon (Exp Center)] Process Created a Thread into lsass Process
The malicious encoded command alert rule
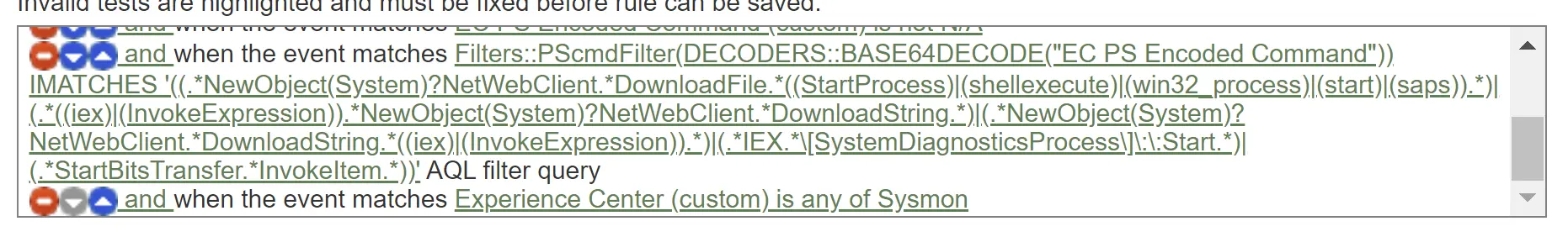
Rule Filter
Filters::PScmdFilter(DECODERS::BASE64DECODE("EC PS Encoded Command")) IMATCHES '((.*NewObject(System)?NetWebClient.*DownloadFile.*((StartProcess)|(shellexecute)|(win32_process)|(start)|(saps)).*)|(.*((iex)|(InvokeExpression)).*NewObject(System)?NetWebClient.*DownloadString.*)|(.*NewObject(System)?NetWebClient.*DownloadString.*((iex)|(InvokeExpression)).*)|(.*IEX.*\[SystemDiagnosticsProcess\]\:\:Start.*)|(.*StartBitsTransfer.*InvokeItem.*))'
AI Analysis: These patterns are designed to catch various forms of obfuscated or encoded PowerShell commands that are commonly used in malware or during penetration testing exercises to download and execute malicious content from the internet.
Offense 6
Time of incident: Apr 19, 2024, 5:59:25 PM
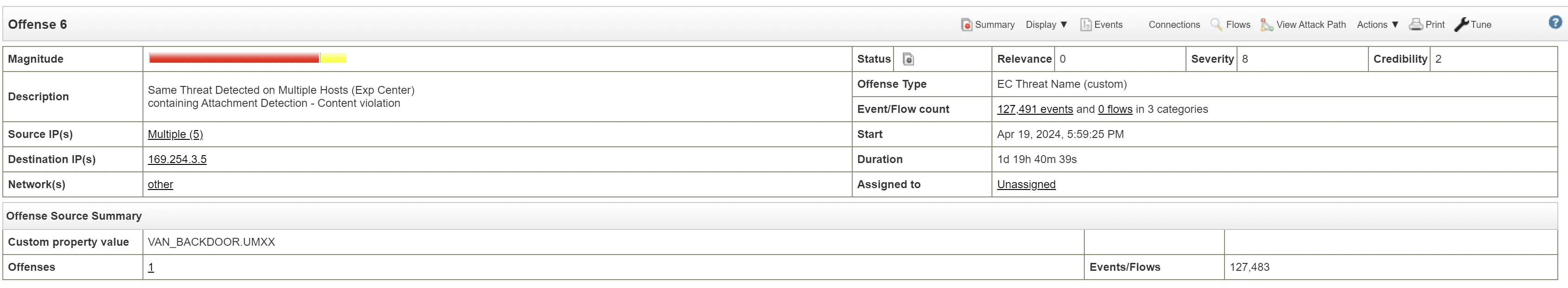
Backdoor Malware: VAN_BACKDOOR.UMXX
Backdoor is located on multiple hosts in the network
Attacker set up persistence and possibly connected to the C2 server
Malware was propagated through a mail attachment via a phishing campaign
Offense 7
Time of incident: Apr 19, 2024, 6:00:07 PM
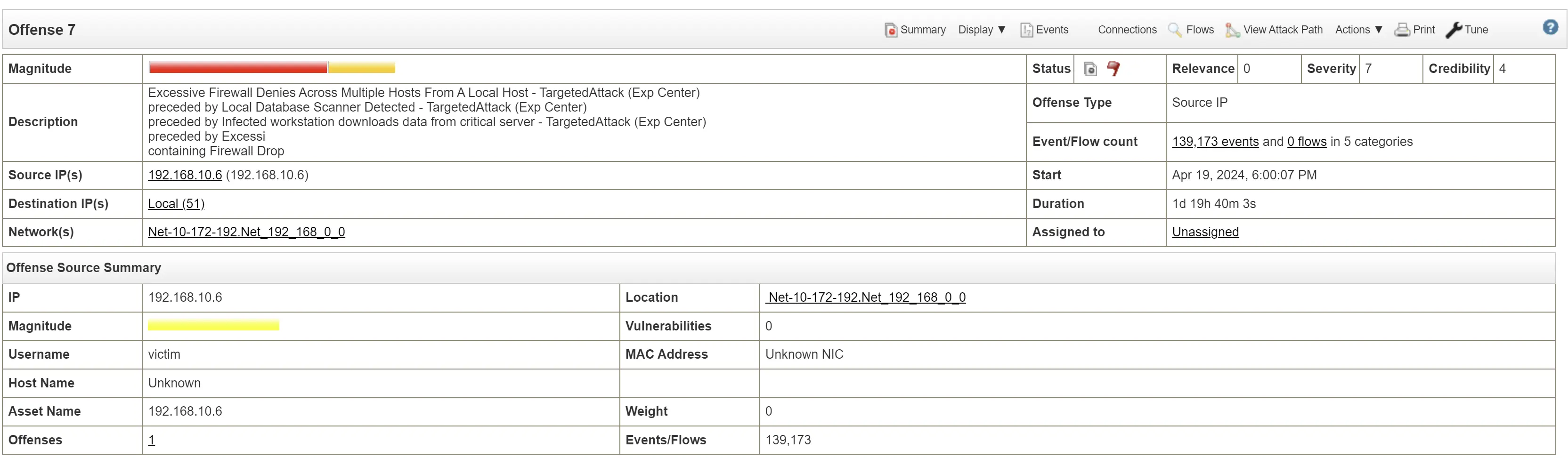
The following sequence of events has been detected, indicating a potential targeted attack:
-
Excessive Firewall Denies Across Multiple Hosts From A Local Host: A local host is attempting to connect to multiple hosts, but the connections are being denied by the firewall, suggesting suspicious activity. (Exp Center)
-
Local Database Scanner Detected: The presence of a database scanning tool on a local host indicates an attempt to probe and gather information from databases within the network. (Exp Center)
-
Infected Workstation Downloads Data From Critical Server: A compromised workstation is downloading data from a critical server, which could signify data exfiltration or unauthorized access. (Exp Center)
-
Firewall Drop: Numerous firewall drop events indicate that the firewall is blocking a high volume of traffic, possibly related to the malicious activities detected. (Exp Center)
This pattern of behavior suggests a coordinated and targeted attack on the network, with multiple stages of intrusion and data extraction.
Infected workstation at 192.168.10.6 is trying to access multiple IP hosts
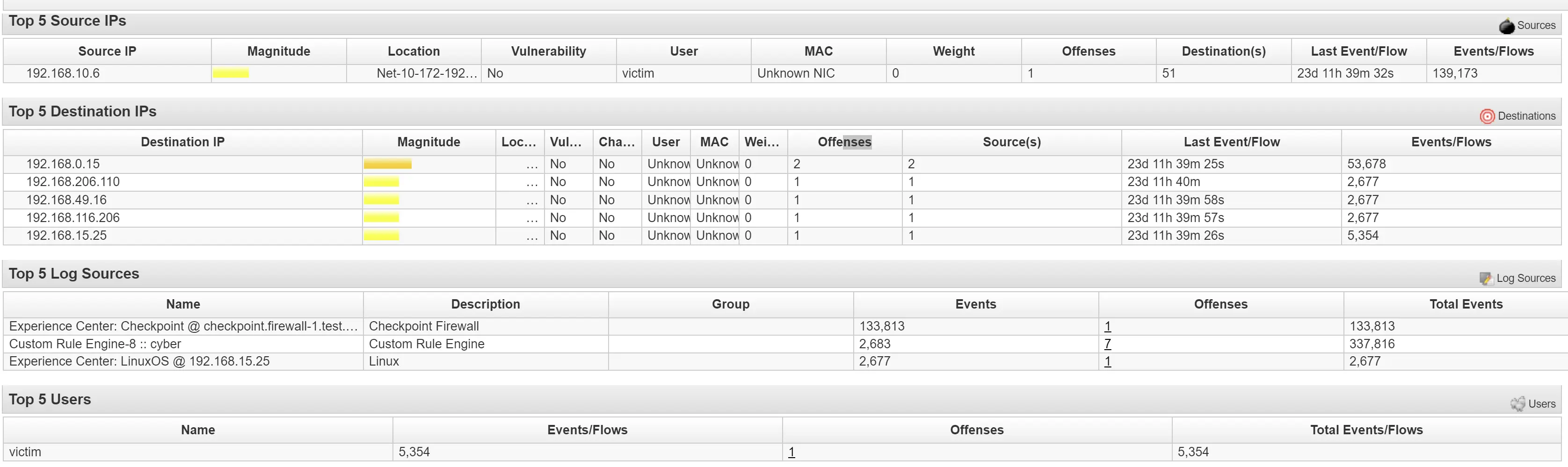
Compromised host used FTP, SFTP, Network Scanners, and database scanners on the local network

Firewall did drop some traffic although there was successful downloads
