Solving a CTF Challenge: Decoding the Secret Message
In this blog post, I will walk you through the steps I took to solve a Capture the Flag (CTF) challenge, where the goal was to decode a hidden message. Below, you'll find a detailed explanation of my process along with screenshots to illustrate each step.
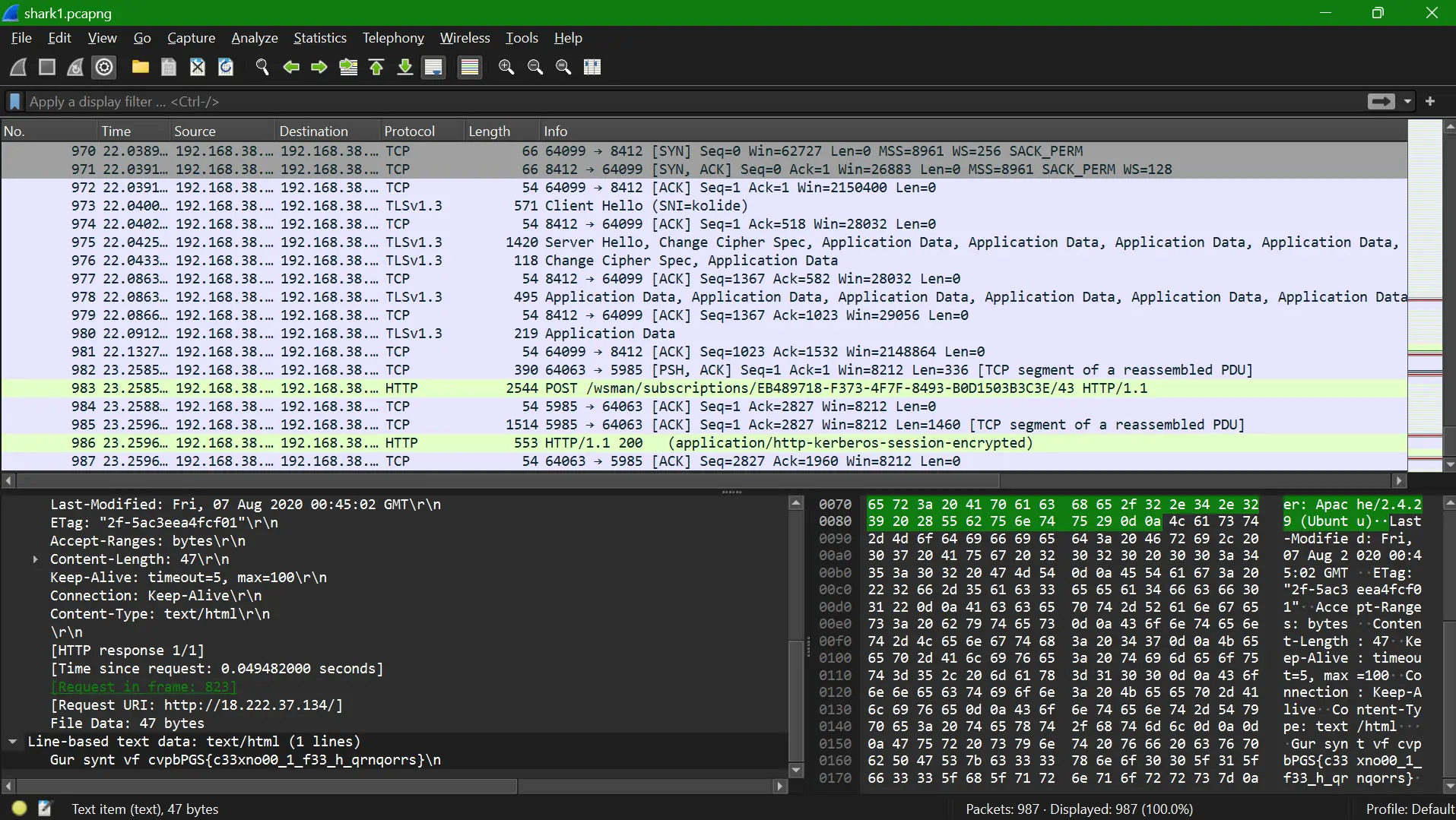
Step 1: Analyzing the Packet Capture
The first step was to examine the packet capture file (shark1.pcapng) using Wireshark. By following the TCP stream for stream 5, I was able to isolate the relevant HTTP traffic.
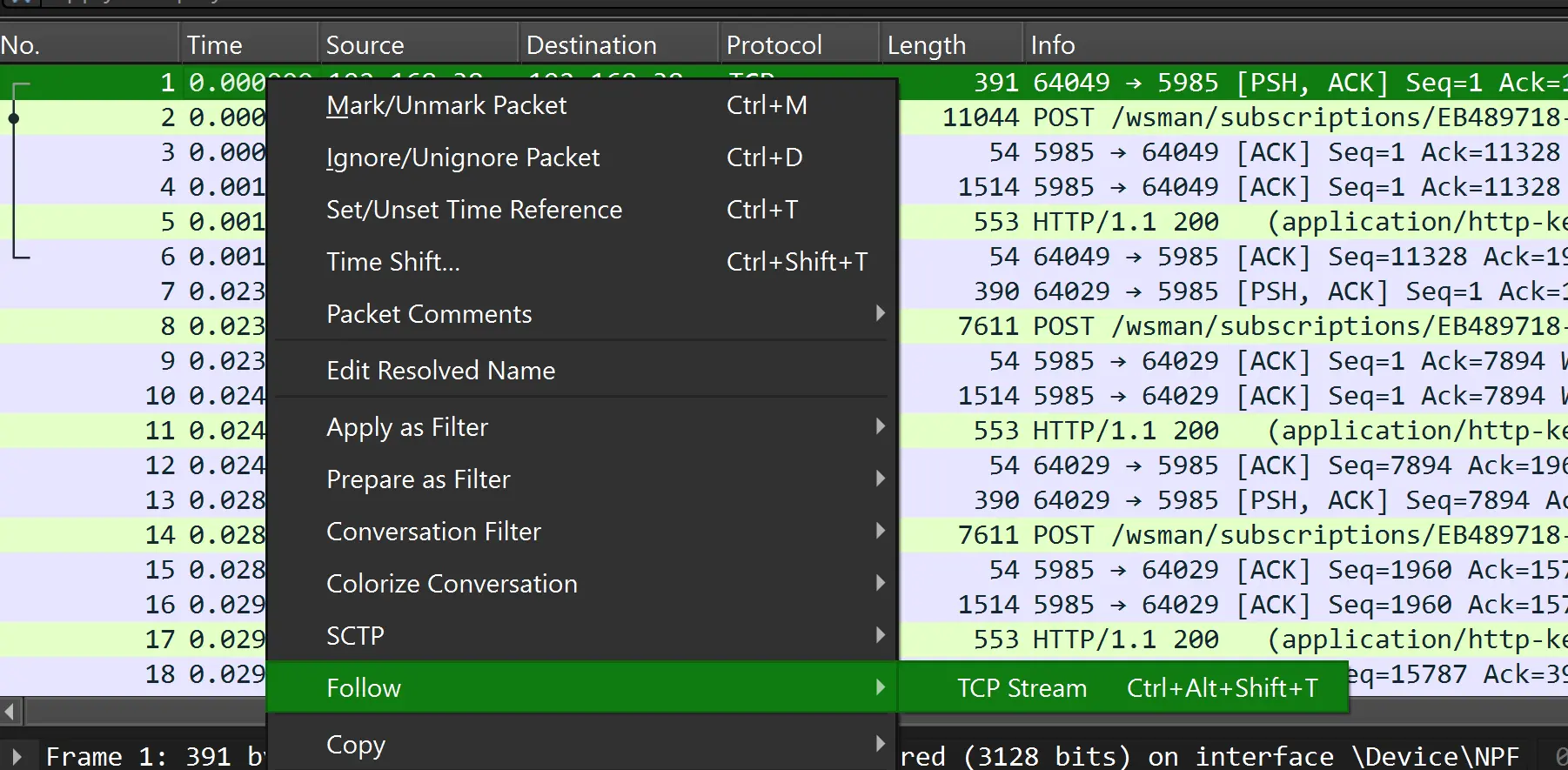
In the stream, I found the following encoded message:
Gur synt vf cvpbPGS{c33xno00_1_f33_h_qrnqorrs}
Step 2: Identifying the Cipher
To determine the type of cipher used, I turned to quipqiup, an online cryptogram solver, to check for multiple patterns.
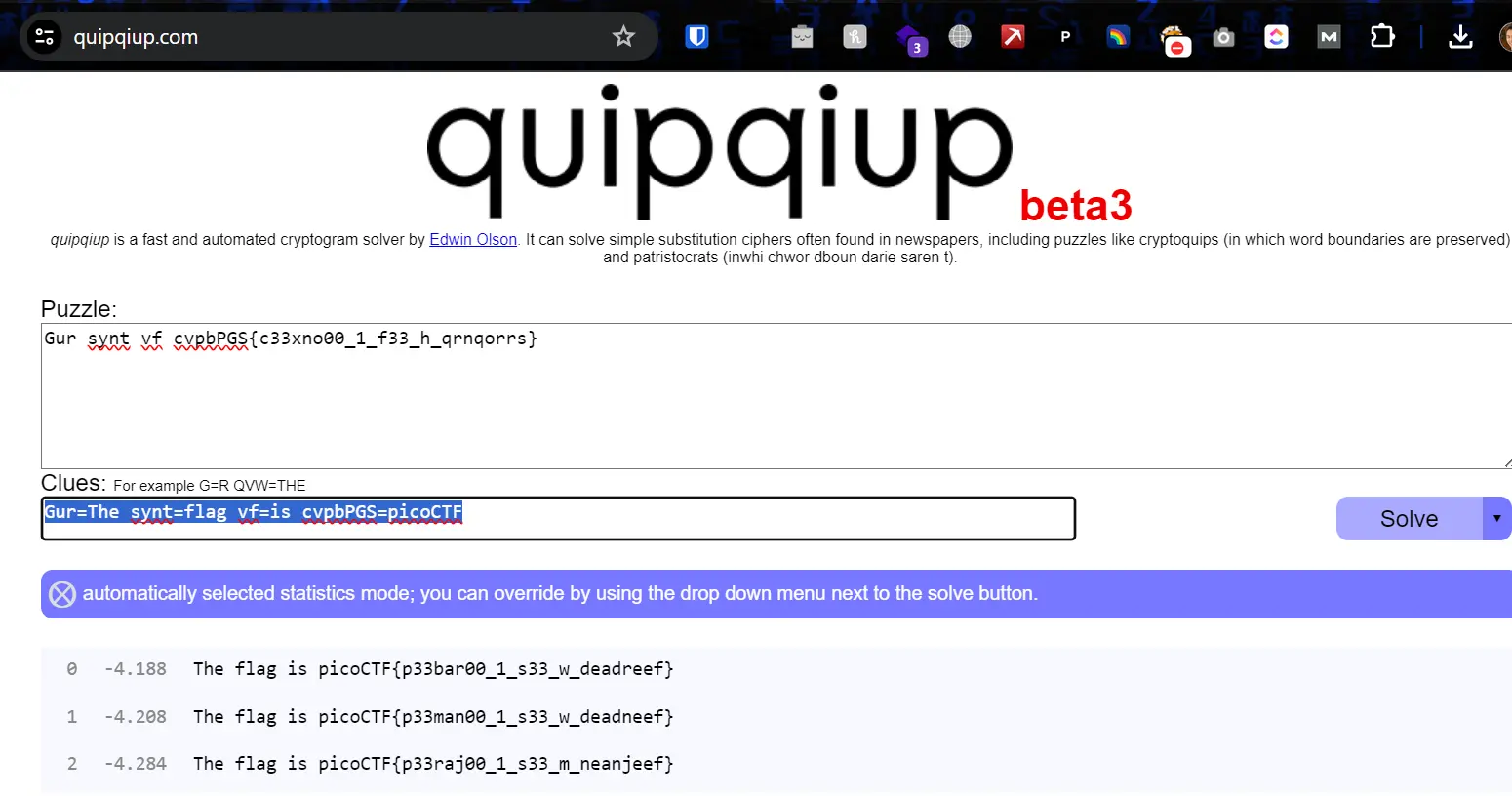
By inputting the encoded message into quipqiup, I noticed that it suggested the message might be a form of substitution cipher. Specifically, it hinted at ROT13, a simple substitution cipher where each letter is replaced by the letter 13 positions ahead in the alphabet.
Step 3: Using CyberChef for Decryption
Next, I went to CyberChef, a versatile online tool for encryption, encoding, and data analysis. Here, I configured it to perform a ROT13 decryption.
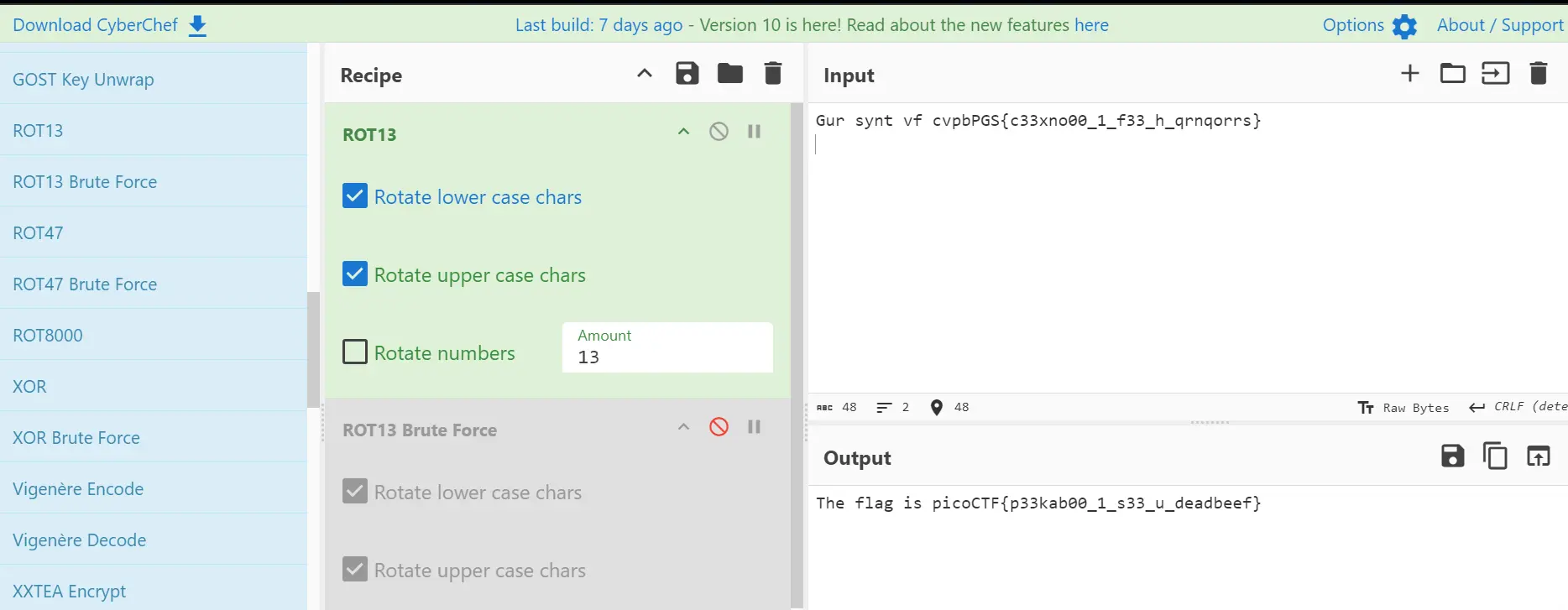
After setting CyberChef to rotate both upper and lower case characters by 13 positions, the encoded message was successfully decoded.
The Final Message
The decoded message from CyberChef was:
The flag is picoCTF{p33kab00_1_s33_u_deadbeef}
Conclusion
By following these steps:
- Using Wireshark to isolate the encoded message.
- Utilizing quipqiup to identify the type of substitution cipher.
- Employing CyberChef to perform the ROT13 decryption.
I was able to decode the message and retrieve the flag for the CTF challenge. This process highlights the utility of different tools in solving cryptographic puzzles and the importance of methodical analysis in cybersecurity tasks.
