Backupbuddy is an intermediate-level challenge from the OffSec Playground, perfect for those aiming for their OSCP. It’s designed to test your enumeration skills, particularly web enumeration, to uncover vulnerabilities. The lab includes exploiting local file inclusion and leveraging crontabs for unauthorized access. The main goal is to understand and exploit these vulnerabilities to build stronger security awareness.
In this walkthrough, I’ll guide you through the process of compromising BackupBuddy, hosted on the OffSec Proving Grounds. The journey begins with a simple PHP file manager that used default credentials. The site was vulnerable to a directory traversal attack, which exposed an SSH key and granted a user shell. From there, a vulnerable SUID binary revealed a shared library misconfiguration, ultimately leading to a root shell. Let’s dive in!
To get started, I’ll run my go-to nmap scan to enumerate services and versions on all ports quickly. I’ll also save the scan results for easy reference later.
nmap -sC -sV -p- --min-rate 10000 192.168.188.43

From the output, it’s clear this is an Ubuntu Linux machine with SSH running on port 22 and an Apache web server on port 80. The logical starting point is to take a closer look at the web server.
It’s a really simple login page with a link to PHP File Manager. Clicking on the link redirects you to the Github hosting the source code. This appears to be the core of Tiny PHP file manager.

The first thing that stands out is how outdated the code is, which might work to my advantage. I checked the Issues and Security tabs on the GitHub repository, hoping to find some low-hanging fruit, but unfortunately, nothing of interest turned up.


Looking back at the README.md, I noticed that the application comes with default creds. Definitely worth checking.
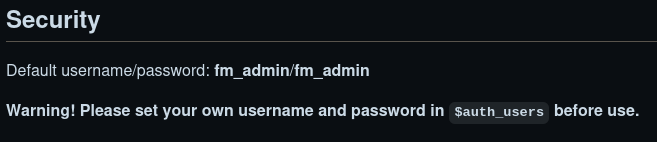
Make a note of those credentials and head back to the login prompt to try them out.

So, it worked.

It’s clear this site is running PHP, and since it’s a file manager, I wanted to check if there was an option to upload a PHP script for command injection. Unfortunately, there isn’t.
Clicking into the Backup section, all I found was a stock photo. Interestingly, you can find the exact image by searching its name on Google.

The same photo is also located in the important_images directory. Notably, both images are owned by a user named Brian.

Clicking on the image reveals the full path of where the file is stored on the web server.

While exploring the site, I noticed that every destination is accessed using the p parameter, formatted in a directory traversal style. The Unicode representation for “/” is %2F, which is used in the URLs.

I attempted a directory traversal attack to access /etc/passwd by entering p=backup/../../../../etc/passwd. Unfortunately, it didn’t work—the parameter was cleared, leaving it blank.

So, I decided to test a simpler approach by trying to move back a directory with p=backup/../../ or even just p=../../.
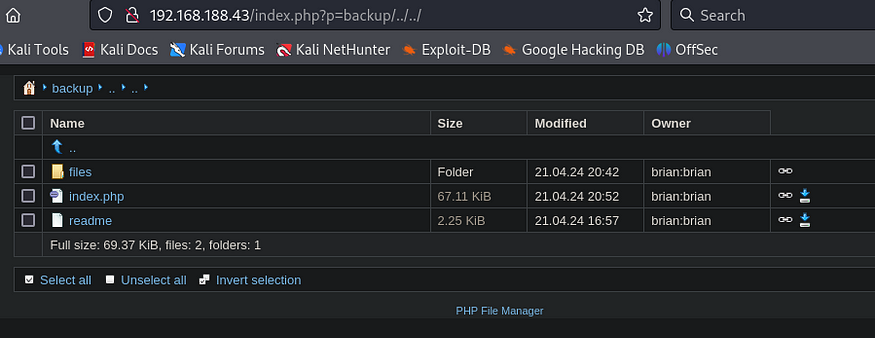
I successfully broke out of the backup directory. With this newfound ability, I can now view any file on the machine that’s accessible to Brian. This includes navigating all the way to the root directory (/).

My first move was to search for ways to get a shell. The most promising option seemed to be checking if Brian had an SSH key in his home folder, so I headed there first.

