In today’s complex cybersecurity landscape, no organization can afford to work in isolation. For threat hunters, success hinges on two key factors: timely intelligence and effective communication. In Module 3 of the OffSec TH-200 course, I explored the importance of inbound and outbound communication, the role of threat intelligence, and the essential Traffic Light Protocol (TLP) for sharing sensitive information securely.
But how do these concepts play out in the real world?
Let’s walk through a scenario where the lessons from this module are critical in preventing a potentially catastrophic data breach.
Inbound Communication: Intelligence Feeds the Hunt
Scenario: A Threat to Financial Services
Imagine you’re a threat hunter for a major financial institution. One day, while reviewing threat intelligence feeds, you notice operational intelligence indicating chatter on the dark web about a new campaign targeting financial institutions. The chatter mentions a specific banking trojan known as Emotet, which has been revamped with advanced Tactics, Techniques, and Procedures (TTPs).
Your team immediately flags this intelligence and starts investigating potential entry points. This type of information, classified as Operational Threat Intelligence, provides a valuable early warning system. It allows your team to look for specific Indicators of Compromise (IoCs) such as suspicious IP addresses, domains, and file hashes associated with Emotet. As this intel comes in real-time, it gives your team a head start on detecting and preventing a breach.
This information isn’t isolated; it’s part of a wider landscape that includes Strategic, Tactical, and Technical Threat Intelligence. Let’s break it down:
- Strategic Intelligence: The long-term view — how threat actors, like those behind Emotet, may align with adversary groups that target sectors like finance. This is critical for risk assessments and executive briefings.
- Tactical Intelligence: Focused on the specific TTPs used by Emotet. Knowing their tactics (e.g., phishing emails with malicious attachments) helps your threat hunters craft the right strategies to detect and prevent breaches.
- Technical Intelligence: Specific details like the hashes of Emotet malware, malicious URLs, and C2 server IPs, which help detect the trojan at the technical level.
These multiple forms of intelligence feed into your Security Information and Event Management (SIEM) systems and Intrusion Detection Systems (IDS), where you can correlate incoming alerts to specific IoCs associated with Emotet. Armed with this knowledge, you can move quickly, checking for any signs of activity in your network and locking down potential vulnerabilities.
The Traffic Light Protocol: Sharing Intel Wisely
Scenario: Containing a Leak While Keeping the Right People Informed
Now that you’ve identified a potential threat, the next step is communication. But how do you control who gets the information and when? Enter the Traffic Light Protocol (TLP).
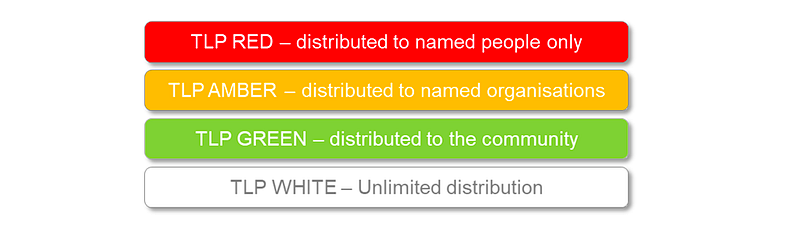
Imagine during your investigation, you find evidence that Emotet has penetrated one of your networks. This is sensitive information that needs to be handled with care. Sharing it too widely could cause panic or even tip off the attackers.